



The increasing need for security in microcontrollers Security has long been a significant challenge in microcontroller applications(MCUs). Traditionally, many microcontroller systems did not have strong security measures against remote attacks as most of them are not connected to the Internet, and many microcontrollers are deemed to be cheap and simple. With the growth of IoT (Internet of Things), security in low cost microcontrollers moved toward the spotlight and the security requirements of these IoT devices are now just as critical as high-end systems due to:
In order to strengthen security measures and make it easier to develop secure solutions in small embedded systems like microcontrollers, ARM released the Cortex®-M23 and Cortex-M33 processors.
There is a new trend for connecting microcontrollers to cloud based services and this is creating a big challenge for the industry: how do we build in robust security at the lowest cost points? In recent years, many IoT-focused microcontroller products were designed with security features, such as crypto engines, secure storage and other hardware features like true random number generators (TRNG).
These features address some parts of the security requirements, such as secure communications, but are not able to address some other challenges. For example, vulnerabilities in applications could still result in a compromise of the whole system. In order to strengthen security measures and make it easier to develop secure solutions in small embedded systems like microcontrollers, ARM released the Cortex®-M23 and Cortex-M33 processors, which are based on a new ARMv8-M architecture release. One of the key features in the newer architecture is the introduction of a security extension called Trust- Zone for ARMv8-M.
TrustZone technology is already being used in billions of high-end embedded systems with Cortex-A processors. To allow it to be used in small embedded systems, TrustZone has been redesigned and optimized for the requirements in microcontrollers.
TrustZone for ARMv8-M is an optional security extension that is deeply integrated within the processor and across various parts of the chips. For example, security measures are deployed in memory access control, bus interface, exception handling (e.g. interrupts) and debug features. When it is implemented, it provides an extra protected execution environment called Secure world, in addition to the normal execution environment (Non-secure world).
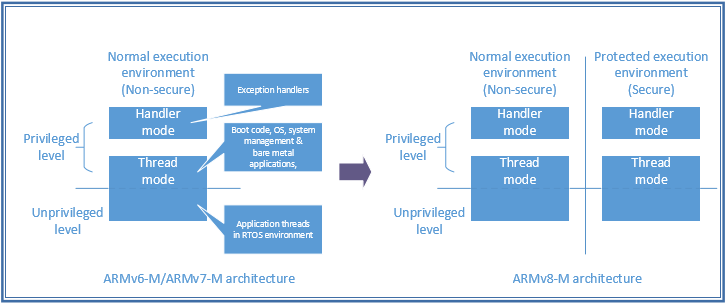
Software running in Secure world can access to both Secure and Non-secure memories and resources, but Non-secure world can access only Non-secure memories and resources. The normal execution environment (Non-secure world) is mostly unchanged from previous Cortex-M processors, and most applications that are written for previous Cortex-M processors can run in the Non-secure world with no or minimal modifications (e.g. RTOS need to be updated).
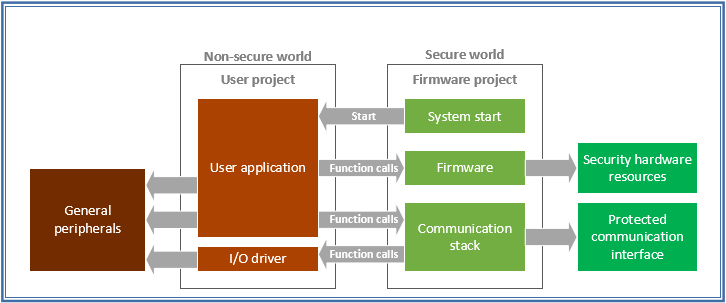
The additional protected environment provides a way for security-critical operations and resources to be protected. At the same time, however, security features can still be accessed by normal applications via protected Application Programming Interfaces (APIs), since the architecture allows direct function calls to take place between security domain boundaries with tiny overhead. To enable Root-of-Trust security, the processor starts up in Secure state. After security management blocks are programmed (e.g. configuration of memory partitioning and interrupt assignments), the secure software can then execute the start-up code in the Non-secure world.
There is a new trend for connecting microcontrollers to cloud based services and this is creating a big challenge for the industry: how do we build in robust security at the lowest cost points?
For the Non-secure world applications, it can run in the same way as traditional embedded applications, with full control on its memories, peripherals, interrupt control and the Non-secure MPU (Memory Protection Unit). However, it is also possible to make use of other APIs provided in secure firmware to access other features. Optionally, Secure firmware can also make use of other I/O driver libraries that could be placed in Non-secure memory.
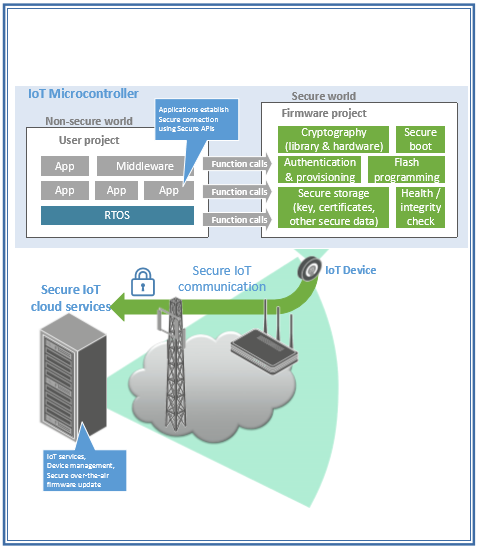
To better understand TrustZone’s capabilities, let us look at an example of a secure IoT microcontroller with IoT connectivity. In such an example device, the IoT connectivity APIs, crypto engine and its APIs, integrity check (heath check) and flash programming are all protected in the Secure world.
Application developers only need to call the APIs to establish a secure connection to IoT cloud services, and the cloud services deliver IoT application services, device management and firmware update mechanism to the IoT devices.
In a design like this, there are benefits to multiple parties:
With the growth of IoT (Internet of Things), security in low cost microcontrollers moved toward the spotlight and the security requirements of these IoT devices are now just as critical as high-end systems
Traditionally, this means the attacker could modify the flash and the device would be unrecoverable remotely. In this instance, the IoT device would need to be replaced or an engineer would need to be on site to reprogram the flash both of which are costly.

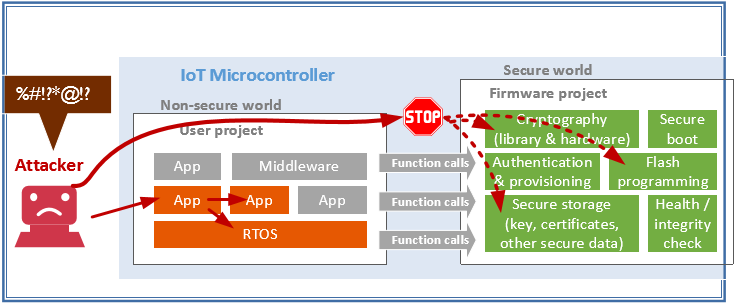
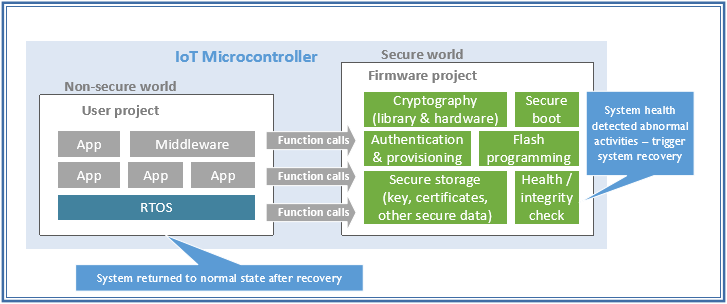
However, with an IoT microcontroller with security protection using TrustZone, the attacker:
And if system health check service is running in the background, the service can detect abnormal system behaviour and trigger system recovery actions. Since the flash memory has not been corrupted, the system can be recovered by a system reset. As a result, the attack is short-lived and the system can be recovered quickly, without any lost/leakage of secure data.
In recently years, even before TrustZone technology was available, microcontroller vendors already started to preload firmware into microcontroller products. The trend of including firmware onchip is expected to become even more common, since TrustZone enables chip vendors to protect valuable software IP, such as Bluetooth and Zigbee stacks, as well as other libraries, like cryptography and sensor-fusion algorithms.
A potential secondary effect is that more microcontroller vendors will be selling IoT software platforms in chips these platforms will have several tightly integrated IoT firmware components, including networking stack (e.g.TCP/IP).
There is a new trend for connecting microcontrollers to cloud based services and this is creating a big challenge for the industry: how do we build in robust security at the lowest cost points?
Today, we see a number of RTOS vendors already providing these IoT software platforms and delivering these software as on-chip firmware could be one way to allow chip vendors to differentiate by providing additional value to their products.
The trend of delivering IoT platformon- chip might also enable new business models for chip vendors. As a part of the IoT platform offering, the microcontrollers can be configured to connect to specific IoT cloud services, potentially allow chip vendors to develop new business model based on IoT services.
Potentially, these IoT cloud services could also be run by cloud operators, OEMs or mobile carriers. These companies could work with microcontroller vendors to create customised IoT microcontroller chips that are linked to specific IoT service platforms.
Using the same silicon chip design, each new IoT cloud services will only need customised preloaded firmware, and application developers can deliver IoT product solutions rapidly by calling preloaded APIs to establish secure connections.
For the end users of embedded products, the race of delivering secure IoT solutions in the microcontroller industry means that new products will likely utilize advance security measures. TrustZone technology for microcontrollers makes embedded security even easier to attain; this means that lowcost microcontroller systems no longer need to be labelled as insecure, as advanced security is now in reach of even the smallest IoT devices. As with the adoption of 32-bit processors in the microcontroller world, the transformation to more secure devices may take some time – but rest assured, the race for delivering secure IoT solutions is on, and the transformation of microcontroller industry has already started.