



The explosive growth in the number of mobile devices, especially smart-phone and tablet family of devices has been well recognized. The fact that most of the Internet users primarily rely upon wireless network technologies for access is also established. The mobile user traffic is predominantly from video-based applications (such as streaming, etc.). There is also contributions to the high network traffic from gaming, virtual-reality, vehicular communications, and other high-bandwidth applications. In addition, these applications also require low-latency for enhanced user experience.
At the same time, there has been significant interest in deploying billions (and more) of small devices, broadly classified as the “Internet of Things”. These are also expected to generate significant amount of network traffic with applications ranging from Smart Manufacturing and Smart Power Grids to Smart Healthcare and Smart Cities. These include communication models such as Machine-to-Machine (M2M) and Device-to-Device (D2D) Communications. Thus, the demands for supporting high-bandwidth connections with low-latency has been increasing for the past few years. A summary of different user group’s perspectives on future mobile traffic demands is available in [1].
To address these needs, the 3GPP standards group has been working on developing a new set of standards, collectively referred to as the 5G cellular network standards.
The standards address different aspects of the network including several novel: (i) physical layer (PHY) technologies including Massive-MIMO, adaptive beamforming, and so on (ii) Radio Access Network (RAN) technologies including Cloud-based RANS [2] and edge- and fog-computing; (iii) Evolved Packet Core (EPC) network architectures based on software defined networking (SDN) and Network Function Virtualization (NFV) technologies, including Network Slicing and programmable control and data planes; and
(iv) Application development frameworks.
This paper presents a high-level summary of some of these important aspects. Section II presents the key network architectural components of the 5G network. Section III presents the NG-RAN technology standards. Section IV presents the EPC architectural components, while Section V provides additional details on Network Slicing. Section VI provides a brief discussion of some of the key challenges faced in realizing 5G networks and concludes the paper.
This section presents an overview of the 5G application-level requirements and the network architecture.
A. Service Requirements
A set of requirements has been defined as part of the IMT-2020 specifications in 2017 [3] and in the 3GPP standards [4]. There are three major application/service categories specified: (i) Enhanced Mobile Broadband (eMBB), (ii) Massive Mac machine Type communications (MMTC), and (iii) Ultra-reliable and low-latency communications (URLLC).
Each of these services has very different performance requirements and traffic demands for network control functions. Each service dimension requires its own set of control functions, existing mobile networks has tightly coupled control functions with fixed interfaces. This kind of tightly bound network functions would increase the Operations and Management costs. This would require 5G to be more flexible and customizable control network functions. The type of applications range from Traditional Voice/Data applications, 3D Video, Cloud-based applications, Smart Home and Smart Building applications, Smart City applications, Industrial Automation and mission-critical applications to self-driving vehicles.
Some of the key technical requirements are: (i) Bandwidth requirement of at least 100 MHz, (ii) Bandwidth up to 1 GHz for frequencies above 6 GHz; (iii) Peak downlink and uplink data rates of at least 20 Gbps and 10 Gbps respectively; (iv) low-latency of the order of milli-seconds; (v) support for up to 500 Kmph user mobility on high-speed trains; (vi) Downlink and peak spectral efficiency of at least 30 and 15 bit/s/Hz respectively; (vii) Target downlink and uplink “user experienced data rate” in Dense Urban scenarios of 100 and 50 Mbps respectively; and (viii) control plane latency under 20 ms, with 10 ms preferred.
In response, the 3GPP 5G standards (Release-15, planned in late 2018) defines two frequency bands: below 6 GHz and milli-metre wave (24-86 GHz). The important components and layers of the 5G Wireless network architecture, that will help realize the 5G network, include the Radio Access Network (RAN) and the Evolved Packet Core (EPC).
B. Radio Access Network (RAN)
The RAN component consists of the following layers:
1) The Physical (PHY) Layer, that deals with communications over the wireless channel. This channel is used between the user equipment (UE) and the remote radio head (RRH) unit on the enodeB or gNodeB, i.e. the base station. The RRH unit is in turn connected to the Baseband unit (BBU) that processes the baseband signals with the help of a digital signal processor (DSP) for traffic to and from the UE. The PHY layer radio access technology network is referred to as New Radio (NR) in 5G networks.
The main functionalities include symbol transmission on the channel and related ones such as signaling, channel quality measurements and support for hybrid automatic repeat request (ARQ).
2) The medium access control layer (MAC) resides above the PHY layer and utilizes the latter’s services. The MAC layer’s primary functionalities include logical-to-transport channel mapping, multiplexing, de-multiplexing, and error control.
3) The radio link control (RLC) layer functionalities include radio resource allocation using scheduling algo-rithms and data transfer.
Essentially, the RAN takes care of sending the UE’s packets to and from the EPC. The EPC then forwards the packets to the external Internet and vice-versa. This paper does not deal with the RAN aspects, except for the Next Generation RAN (NG-RAN) aspects described in Section III. The reader is referred to [1] for additional details about the PHY/MAC/RLC layers.
C. 5G Evolved Packet Core
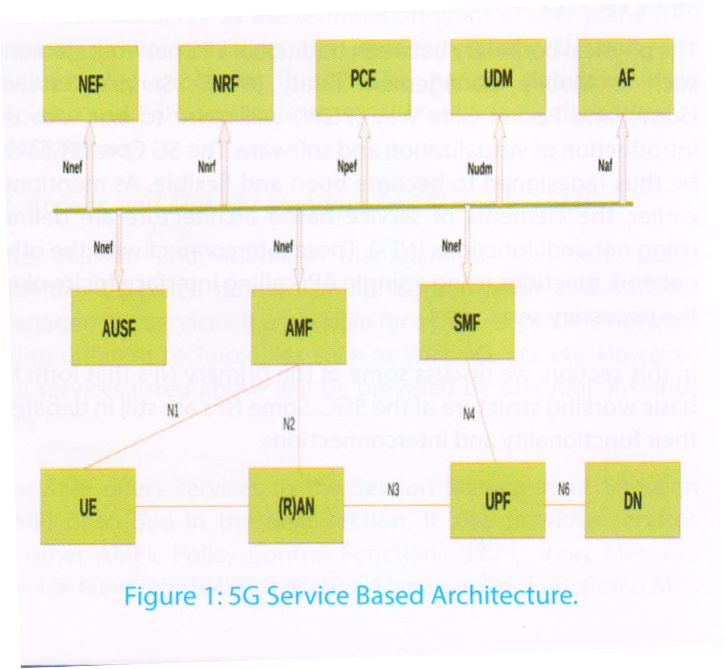
With current heterogeneity of radio technologies, multi dimensional services [4] and considering the current softwarization and data-plane innovations [5] a new core network was defined, which would support known and unknown use cases for 5G. This new core network is called Next Generation Core (NGC). The 3GPP Release-15 document specifies the service-based representation as shown in Figure 1. This is referred to as the Service-Based Architecture (SBA) and is to be adopted in 5G systems.
The interactions from front end to the NGC is represented in two ways: (i) Interactions among the control plane network functions within the core; (ii) Interactions between Radio Access Network (RAN) Network Functions and 5GC Network Functions. Network Functions within the 5G control plane (CP) will use service-based interfaces for their interactions. The User Plane (UP) functions and radio interactions shall continue to use the reference point interfaces.
The 5G standard also includes the concepts Control Plane/User Plane (CP/UP) separation (CUPS) and Network Slicing (NS). Network slicing discussed in Section V in more detail.
The functional architecture of 5G core is flexibly designed with intentions to adopt any implementation changes. The entities in the 5G core network within the control plane enables cross-domain interactions allowing other authorized network functions to access their services. This structure would allow custom based communications or leverage communication with HTTP based APIs, replacing protocols such as Diameter [6]. The 5G SBA would create an independence with NR, allowing standalone mode without dependency on legacy networks [7]. The slicing approach would form the custom QoE models for UE allowing different cost models also allow services like single UE simultaneously connecting to multiple services over multiple slices with optimized access and mobility signaling. The mobility management can be made custom to allow different range options to the users, also allowing a demand based mobility, which led a new service direction called Mobility Management as a Service (MMaaS) [8].
A service requirement in 5G network architecture is defined as a set of independent interacting functional units (that are referred to as Network Functions (NF)). Each NF can service several dimensions of service requirements if they share some functional part in common. This requires a separate demarcation at NF to distinguish different flows. For such management and operations entities are defined in 5G Core to make the operations plain sailing. This kind of abstraction ensure potential upgrades or addition of new NF would not effect the existing network services. This network services or NF can be virtualized which we call as Virtual Network Function (VNF) and managed by a service called Network Function Virtualization (NFV) [9], which would help implement the OAM of VNFs.
The 5G core is defined with several functional entities, each functional entity is a set of several NFs. The primary network functions are discussed in Section IV. The typical 5G architecture divides into three parts: Front-haul, Mid-Haul, and 5G-Core. The evolution of RAN discussed in Section III has created a mid-haul entity to the previous 4G mobile networks.
This section describes the basic concepts of Cloud Radio Access Network (C-RAN) and the evolution to next generation RAN (NG-RAN).
A. Cloud-RAN
In early LTE cellular systems, the baseband processing is performed at the radio front-end i.e., near the cellular site. In such architecture, there is difficulty in managing distributed sites and huge operational cost is involved in maintaining the baseband units(BBUs) at each cellular site.
Using software-defined radios, it is possible to implement BBU functions on programmable platforms. Thus, the frontend can be split by moving all the high-level services of baseband to a central pool unit called the Cloud-RAN (C-RAN) [2]. These software-based baseband units executed on a cloud system provide necessary services to the Remote Radio Heads (RRHs) that are deployed at the cell site as shown in [10], [11]. This has generated wide interest both from industry and academia [12]–[16].
However, C-RAN does have its drawbacks. High Fronthaul capacities are needed to address higher bandwidth requirements between BBUs (Base-Band Units) and RRHs. Optical links can be used to address this need, but leads to increased capital expenditures (CAPEX). Also, BBU cooperation is needed to share user data. This requires significant architectural changes to the existing. Further, virtualized interfaces are required to enable unified interactions among heterogeneous networks.
B. Evolution from Cloud-RAN to NG-RAN
A large number of operators are now evaluating Next-Generation RAN (NG-RAN) as a way to meet future service requirements. From the initial days of creating C-RAN, which was business oriented to save operational costs, the architecture has now evolved to meet the future requirement in NG-RAN.
Functional split was one of the topics studied. In FluidNet [17], re-configurable fronthaul that can flexibly support one-to-one and one-to-many logical mappings between Base Band Units (BBUs) and Radio Resource Heads (RRHs) was considered. An optimal functional split is discussed in [18]. Various options for the RAN and its interfaces to the core are described in [7].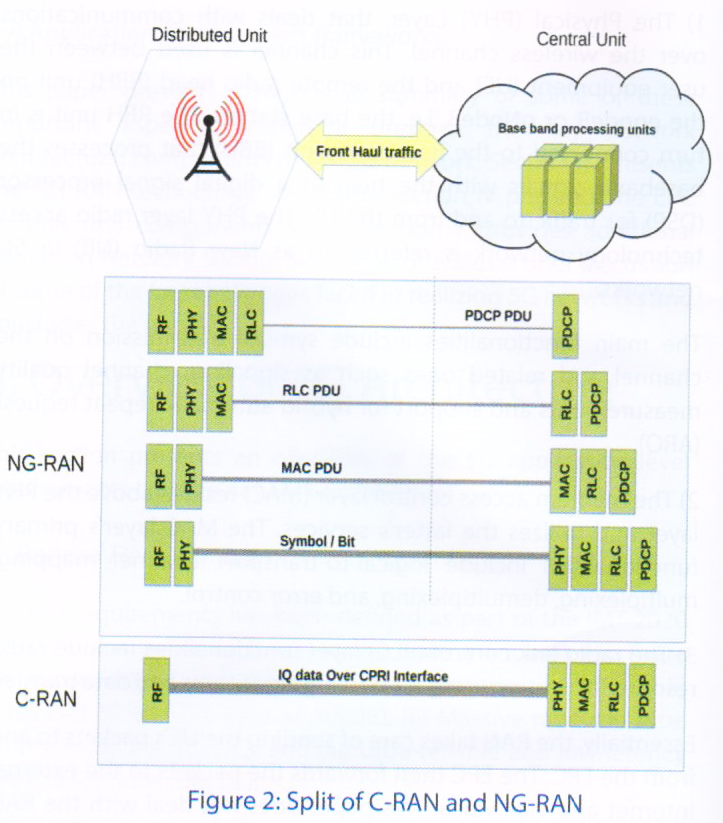
In the NG-RAN architecture, real-time (RT) functions are deployed near the antenna site to manage air interface resources. Also, non-real-time (NRT) control functions are hosted centrally to coordinate transmissions across the coverage area. This functional split concept is shown in Figure 2, that shows a Central Unit (CU) and Distributed Unit (DU). This functional architecture is now native to the 3GPP specification [19].
Implementation of the NGRAN architecture and the subsequent deployment in the network depends on the functional split between distributed radio and centralized control, these we call as DU and CU split. The DU will process low level radio protocol and real-time services while the CU will process non-real-time radio protocols. 3GPP has recognized eight different split options, discussed in [7], of these the most widely discussed two splits, still in debate is discussed in 3GPP status meeting [20].
The different splits is shown in Figure 2. The services of CU and DU can be virtualized and put in Commercial off-the-shelf (COTS) servers, these virtualized network nodes or Virtual Network Functions (VNFs) can be realized with a network architectural concept called Network Function Virtualization (NFV) [21]. NFV offers a new way to design, deploy and manage virtual network nodes. It also enables us to decouple suppliers hardware and software business models, opening new innovations and opportunities for SW integrators. The managing and operational aspects of NG-RAN with CU and DU splits would be plain sailing with NFV. There are several research papers which already attempted in virtualizing mobile network functions [5], [9], [22].
The physical boundary between traditional EPC network elements such as Mobile Management Entity (MME), Service Gateway (SGW), and Packet Gate Way (PGW) will cease to exit with the introduction of virtualization and software. The 5G Core (5GC) can be thus redesigned to become open and flexible. As mentioned earlier, the elements of service based architecture are defined using network functions (NFs). These interconnect with the other network functions using a single API calling interface for invoking the necessary services.
In this section, we discuss some of the primary NFs that form the basic working structure of the 5GC. Some NFs are still in debate of their functionality and interconnections.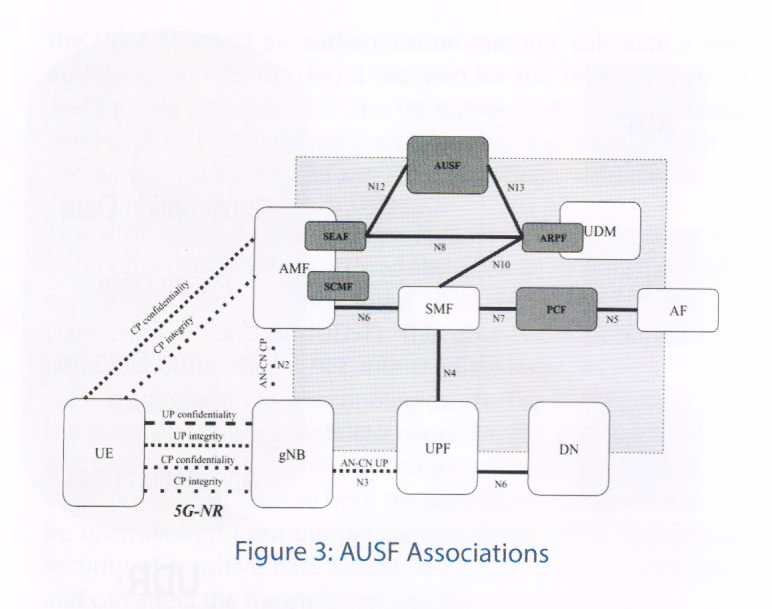
A. Authentication Server Function (AUSF)
The evolution to 5G architecture has involved many network services into the domain. Interactions between network services, when done without proper identity management, would create security gaps in the system.
The AUSF component handles authentication requests for 3GPP access and non-3GPP access networks. This system resides in the operator’s home network. The entities inter-acting with AUSF for identity management is shown in Figure 3. The security architecture and procedures of 5G are discussed in 3GPP Release-15 [23].
The AUSF interacts with the Security Anchor Function (SEAF) in order to authenticate the User Equipment (UE). The set of values in the Universal Subscriber Identification Module (USIM) are used by the Authentication Credential Repository and Processing Function (ARPF). The subscription identifier is used to uniquely identify a subscription and to mutually authenticate the UE and the 5G core network.
The AUSF will serve as the termination point of user plane (UP) security, while providing the necessary authentication and authorization processes. It will also handle network slicing security and Enhanced International Mobile Subscriber Identity (IMSI) Privacy.
B. Access and Mobility Management Function (AMF)
The Access and Mobility Management Function (AMF) provides UE-based authentication, authorization and mobility management services. It is possible for a UE to access the network using different technologies such as WiFi, 4G, 5G, etc. However, the services listed above will be provided by one AMF instance [24].
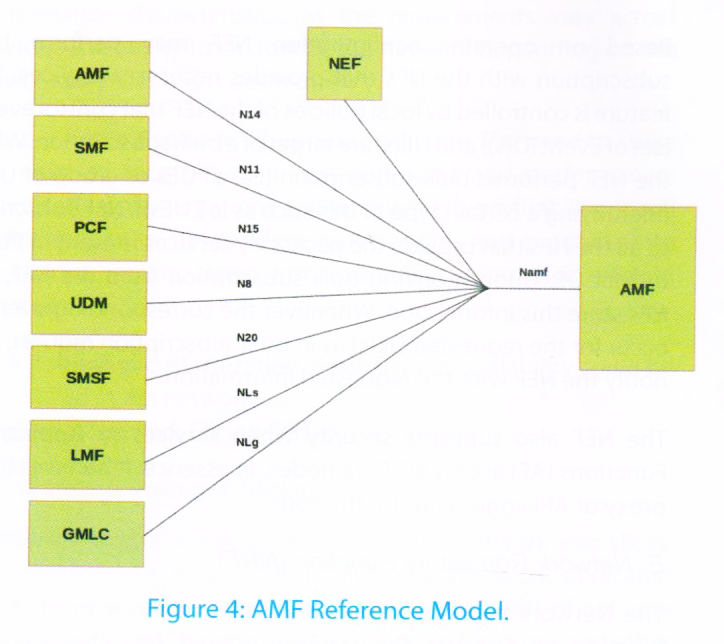
The AMF offers services to the Session Management Function (SMF) described in the next section. It also provides services to other AMFs, Policy Control Functions (PCF), Short Message Service Function (SMSF), Location Management Function (LMF), Gateway Mobile Location Centre (GMLC) and NEF via the Name of service based interface [25], [26] as shown in Figure 4.
Some of the key AMF services include registration, connection, reachability and mobility management. It also serves as termination points for RAN control-plane interface (N2). It also supports transport of session management messages between UE and SMF. It provides several other functions that are too detailed to list here.
C. Session Management Function (SMF)
The Session Management Function (SMF), as the name implies, handles management of UE sessions while also allocating IP addresses to UEs. It also selects and controls the UPF for data transfer. Per-session SMFs may be allocated to UEs with multiple sessions. It also interacts with the User Plane Function (UPF) for efficient routing of the user’s packets. The detailed set of functions is discussed in [27].
D. Network Exposure Function (NEF)
The Network Exposure Function (NEF) enables external exposure capabilities of network functions for supporting Monitoring, Provisioning and Policy/Charging. The network capability exposure comprises:
(i) Exposure of network events externally as well as internally towards core network NFs; (ii) Exposure of provisioning capability towards external functions; (iii) Exposure of policy and charging capabilities towards external functions; and (iv) Exposure of core network internal capabilities for analytics.
The Monitoring capability is for monitoring of specific event for UE in 5G System (5GS) and making such monitoring events information available for external exposure via the NEF. The Provisioning capability is for allowing external party to provision of information which can be used for the UE in 5GS. The Policy/Charging capability is for handling QoS and charging policy for the UE based on the request from external party.
Based on operator configuration NEF may perform bulk subscription with the NFs that provides necessary services. This feature is controlled by local policies of the NEF that control events (set of Event ID(s)) and UE(s) are target of a bulk subscription. When the NEF performs bulk subscription (i.e. all UEs or group of UE(s) (identifying a certain type of UEs such as IoT UEs)), NEF subscribes to all the NFs that provide the necessary services present in PLMN to that UE. Upon receiving bulk subscription from the NEF, the NFs store this information. Whenever the corresponding event(s) occur for the requested UE(s) as in bulk subscription request, NFs notify the NEF with the requested information.
The NEF also supports security when services or Application Functions (AF) access 5G Core nodes. In essence, it behaves like a proxy or API aggregator for the core.
E. Network Repository Function (NRF)
The Network repository functions (NRF) allows every network function to discover the services offered by other network functions. It supports the service discovery function by maintaining the set of NF profiles and the set of available NF instances.
A service is an atomized capability in a 5G network, with the characteristics of high-cohesion, loose-coupling, and independent management from other services. This allows individual services to be updated independently with minimal impact to other services and deployed on demand. A service is managed based on the service framework including service registration, service authorization, and service discovery. It provides a comprehensive and highly automated management mechanism implemented by NRF, which greatly reduces the complexity of network maintenance. A service will interact with other services in a light-weight manner.
F. Policy Control Function (PCF)
The Policy Control Function (PCF) governs the network behavior by supporting unified policy framework. It also provides policy rules to Control Plane function(s). For instance, it provides Access and Mobility Management related policies for the AMF; and UE policies for Access Network discovery and selection policies and UE Route Selection Policies.
The PCF is expected to be similar to 4G’s Policy and Charging Rules Function (PCRF) framework. This entity is still not framed in total; the current status is available in [28].
G. Unified Data Repository (UDR) and related functions
The 5G network will serve different service dimensions, collecting data from heterogeneous environments. The Unified Data Repository (UDR) is the network entity in the 5G Core Network (5GC) which stores user subscription data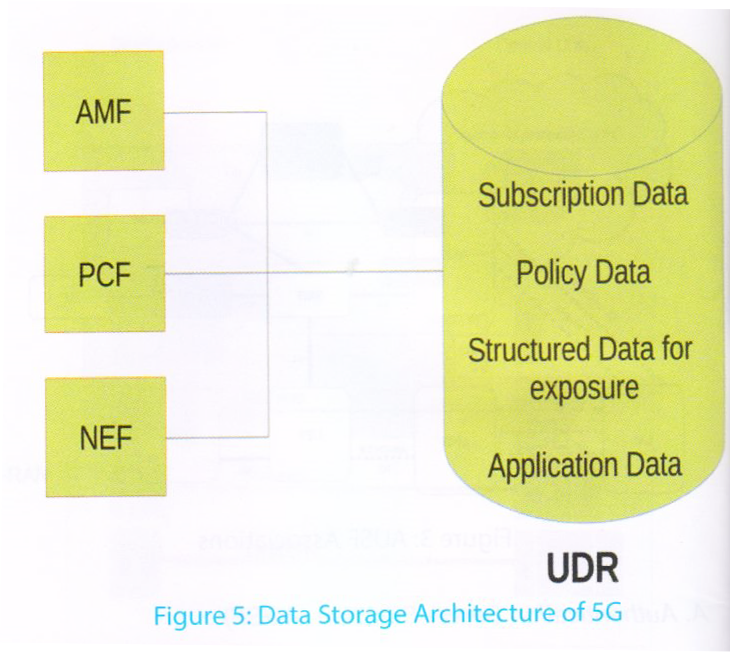
policy data, structured data for exposure, and application-level meta data such as Packet Flow Descriptions (PFDs) [29], [30]. It provides the necessary interfaces for storing and retrieving of data in the repository. It also supports means for subscription to and notification of subscribed data changes.
The data storage architecture for 5GC is shown in Figure 5. The interface is used by other network functions (such as UDM, PCF, and NEF) to access a particular set of the data stored in the UDR. UDR provides one DataRepository service to all of the NF consumers, while different types of data may have different data access authorizations. The UDR will also have an authorization management mechanism to guarantee the safety of data access and the information in the repository.
The operations serviced by UDR should be able to identify the NF type of the consumer and the service operation type or name. It will also indicate the requested data information including the data set and data subset, and the resource/data identifier. If there is an illegal service operation or data access request initiated by a NF consumer, the service failure response will be returned through the corresponding interface with an explicit cause value.
Related to the UDR is the the Unified Data Management (UDM) function. that offers services to AMF, SMF, SMSF, NEF and AUSF. The services include Subscription data storage, Context data management service Authentication service in collaboration with AUSF.
The subscription data management is used by NFs (AMF and SMF) to retrieve the UE’s subscription data relevant to the consumer NF from the UDM. It is also used by consumer NFs to subscribe or un-subscribe to notifications of data change. UDM offers consumer NFs (AMF, SMF, SMSF) that have previously subscribed, to get notified by means of the notification service operation when UDM decides to modify the subscribed data.
The UE Context Management Service is used by NFs to register at the UDM. It is also used by the registered consumer NFs (AMF) to get notified when UDM decides to de-register the registered consumer NF.
The UE Authentication service is used by the AUSF to request the UDM to select an authentication method, calculate a fresh authentication vector (AV) if required for the selected method, and provide it to the AUSF. The UE Authentication service is also used by the AUSF to inform the UDM about the occurrence of a
successful or unsuccessful authentication [23].
The Unstructured Data Storage Function (UDSF) function is a part of the UDM entity described above. Network Functions (NFs) can store/retrieve “unstructured” data from an Unstructured Data Storage Function (UDSF). This data is based on the state information of different NFs, intermediate representation of data crossing different radio technologies, etc. The UDSF is located in the same Public Land MobileNetwork (PLMN) as the NF and can be attached to multiple NFs. The data that NF chooses to store in a UDSF is not unstructured from the perspective of the NF, but can be unstructured from the perspective of the UDSF. In addition, security of sensitive data stored in a UDSF must be considered and can affect the transmission and storage of such data.
H. User Plane Function (UPF)
The UPF implements part of the SGW and PGW functionality from LTE’s EPC. In particular, it supports
packet routing and forwarding, packet inspection, and QoS handling. It also acts as an external PDU session point of interconnection to Data Network (DN), and is an anchor point for intra-RAT and inter-RAT mobility. This is one of the important functions and has to efficiently process packets within sub-milliseconds. Any slowdown in this function will significantly increase packet latency and reduce user’s quality-of-experience. The UPF utilizes the services of the Session Management Function (SMF) explained earlier.
I. Application Function (AF)
The Application Function (AF) enables application influence on traffic routing, accessing NEF, interaction
with policy framework for policy control. This function will have significant trust and security implications since the core functions are exposed to the application level. This function is already part of the LTE standard and hence the experience from 4G networks will help in the 5GC design and implementation. This section presented the important control and dataplane functions in the 5G core network. Network slicing is an important novel function of the architecture. The Network Slice Selection Function (NSSF) is explained in detail in the next section
Next-generation 5G networks will cater to a wide range of new business verticals. It will facilitate
autonomous driving, e-health-care, IoT usage for smart cities, and remote operation of machinery. All such applications require connectivity, but with varying network service characteristics. For instance, the mobile broadband requires high data rates to be supported, whereas a mission-critical service like telesurgery focuses on low latency as a service requirement. The network performance is characterized in terms of latency, availability, data rate, QoS, security and many other parameters. One of the key technical challenges faced by service providers is to deliver this whole spectrum of network performance characteristics, as the requirements vary across services. The ability to customize the network depending on the service specifications is desired.
These services also pose a business challenge. The need to strike the right balance between cost-optimized and performance-optimized implementations will be crucial to profitability. It will enable industries to introduce new services and products into the market rapidly, along with expanding upon their existing services.
Such notions of customization, flexibility and scalability could be introduced in the network using the
concept of Network Slicing [31].
A. Concept of Network Slicing
Network slicing is a way of abstracting the network into slices, each forming an end-to-end logically
isolated network, dedicated to various types of services. Each slice is composed of network functions, the network resources to run these functions and other policy information. For instance, a network can be sliced into a slice for autonomous cars, a slice for smartphones, a slice for IoT devices etc.
Network slicing is driven by the techniques of Software Defined Networking (SDN) [32] and Network Function Virtualization (NFV) [33]. NFV is a network architecture which virtualizes the network functions previously realized on costly hardware platforms as software functions by installing them on a cloud computing environment or on lowcost hardwares. SDN is used in separating the control plane and the user plane, and to enable the control of data.
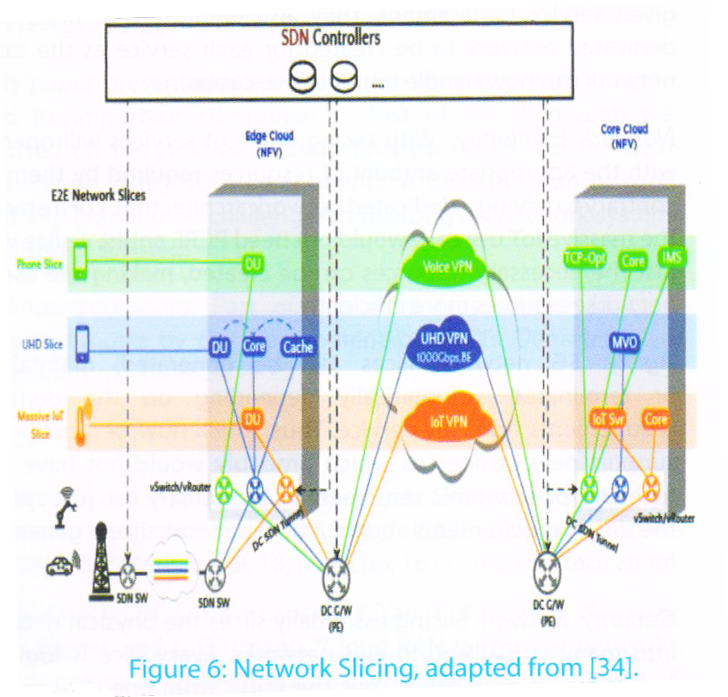
Figure 8 shows various entities involved and the roles they play in network slicing. Network function such
as MME, PCRF and S/P GW in the packet core and DU in RAN are virtualized (NFV) by installing them on Virtual Machines (VMs) which are deployed on a commercial server and not on a dedicated network equipment. SDN helps in the network connectivity between VMs in edge cloud and core clouds. There lies a virtualized server in the core cloud. In the Hypervisor of that server, a router is run. SDN controller creates SDN tunnels between the VMs of core cloud and the router. Similarly tunnels are also created between the VMs of the edge cloud and the router. The mapping of the two tunnels is also handled by the SDN controller thereby, creating an end-to-end network slice.
The combination of NFV and SDN, makes it possible to move parts of the core network closer to the edge or users, thus reducing the end-to-end network latency. In a different use-case of massive IoT slice, the core cloud is made without the mobility management feature which makes it light duty and simpler to support massive connections. The UHD slice is configured such that the 5G core (UP) and the cache server are moved in the edge cloud, enabling high performance video cache.
For different services, the slices could be assigned different types of resources. This provides flexibility in terms of placement of these virtualized network functions as well, allowing the design of slices to meet the service requirements. Together, these slices can support a large number of services and make the operations cost-effective.
B. Benefits
There are several benefits of network slicing, as explained below.
Customized Connectivity. Current mobile networks only provide a particular set of control functions and cannot customize them for a certain service type. 5G networks make the network flexible, enabling the possibility of creating a customized network for a given service requirement. They also eradicate the need of a dedicated network to be created for each service as the same network can now handle multiple use-cases.
Network Efficiency. With slicing different services will operate with the appropriate amount of resources required by them on contrary to having a dedicated network architecture. For instance, the massive IoT use case would not need PCRF entity. A slice with just the necessary resources can be created, making the use of network resources more efficiently.
Agility. 5G network slices can be generated, maintained or terminated automatically depending on the demand requirements from the service. Thus, it will now be possible to support new businesses which probably would not have had technical or economic sense earlier. An industry can just specify the slicing requirements and a suitable network slice is generated for its use.
Security. Network Slicing essentially slices the physical network into many virtual end-to-end networks. Every slice is logically isolated from each other, thus the traffic from one slice cannot interfere the other. Logical isolation also implies that an error or a fault in a particular slice will not effect on the functioning of other slices.
Cost Efficiency. Due to virtualization the network functions earlier realized on costly hardware are now implemented as software function over a low-cost hardware. Also 5G eradicates the need of a dedicated network for each service, since different requirements can be satisfied by multiple logical networks (slices) over a single physical network, making the network cost-effective.
This section describes some of the implementation and research challenges involved in realizing 5G mobile networks.
A modular refactoring of the functionalities of the existing EPC that is carried over into the 5G architecture is needed. In this process, integrating these modular functions with the new 5G EPC functions that are NOT a carry over from the previous generations, is an important problem in deriving the Control Plane or the CP or the C-Plane for 5G. The important aspects such as security, connectivity management and mobility aspects of these control functions of the C-Plane is an important research area. The orchestration aspects as well require a proper and elegant design in this regard. With specific aspects such as Virtual Machine / Container instantiation, assignment and placement in the proper Data Center location whether it be Core, Edge or Site function Data Centers is important. Their consequent movement later on to another location within the DC or across DCs of the said provider depending on traffic load or basic reassignment to cater to different slices also require careful thought of the basic control plane software infrastructure design and implementation.
Migration of some of the important NFs in the C-Plane from one DC to another require careful procedures for moving and consistently maintaining the state required for the Load Balancers and for the NF and their associated Micro-services themselves to be designed and implemented. Clustering a group of NFs, more than one of a variety and instantiating the Service Chain of such related NFs for a Network Slice catering to
a set of UEs thus providing a hybrid Centralised and locally distributed Control Plane of Control Planes (in a sense a hierarchical C-Plane for the CPlaneNFs) is an important requirement to consider to scale the C-Plane controllers.
When building a hierarchy of controllers for the orchestration design points relating to consistency, race condition handling and appropriate connectivity management and security with mobility considerations need to be taken into account. As the envelope is pushed further and further with respect to scalable and flexible design, innovative design points need to be accorded sufficient amount of attention.
Re-use of existing protocols for service chaining such as Segment Routing based MPLS could be accorded attention as well. The reason for that is that each NF instance in the C-Plane would require a label (such as the one used in MPLS) to be assigned to it to be accorded the place and order required by the C-Plane NF in a series of Service Chain events that need to be accorded to a packet going through that service Chain. Segment routing has a natural placeholder for the architecture required to solve this problem. Relevant connectivity of the C-Plane orchestrator with the load-balancers themselves is also important to assign a stack of such labels to a packet entering the Site DC, Edge DC or the Core DC where the direction of the packet is decided when routed through such a service chain. We deal with abstracting the other physical resources such as the Transport and other core items in the physical infrastructure for network slicing in the end of this section.
With regard to the UDM, UDR functionalities providing an appropriate view of the schema that needs to be
exposed to the other related NFs that require services from it, is also to be worked on. The security aspects of such exposure and the required encryption that needs to be done to protect such data flowing is another area of research that needs to be attended to.
Inter-provider agreements between multiple service providers would require a restricted view and appropriate security for the data flowing in and out of the UDR module and appropriate procedures put in place for the request and reply protocols for such subscriber data. Caching of such data in the appropriate DCs involved would also require careful attention and solutions for keeping the caches consistent would have to be tied together in the solution as well.
Service discovery for the NFs in the C-Plane is another important work item to be considered. An array of
cloud solutions are available for this and choosing the appropriate one requires careful attention. A dynamic generation of DNS records based on the refactoring and movement of the individual NF instances as they appear and disappear and reappear elsewhere in the network could be a possible solution for this problem. Slice monitoring and assignment of the individual NFs to the respective slices created and destroyed requires careful design and implementation. The solution should be scalable and more importantly be flexible.
The Management and Orchestration of the C-Plane NFs and the D-Plane resources in consort with each
other taking into account the proximity considerations and the load factor is an important aspect as well.
Another important aspect is online and offline charging and the related policies that need to be applied for QoS and QoE of the individual services offered for a UE is another important aspect. Proper and consistent and errorless accounting of the packets being maneuvered through different slices in the network is primary to the proper operation of the services.
Traffic detection frameworks that need to be deployed need to be given proper consideration. The TDF
functions in the 5G core need to be scalable and appropriately flexible to work in consortium with any network slice in operation. Slice creation orchestration with appropriate attention to the load of the various NFs instantiated should be a distributed solution and appropriately centralized to the extent to make a proper and informed decision as to which NFs to assign to each slice and for appropriate scale up and down decisions.
With concept of network slicing creating a picture where it is NOT only the C-Plane functions that need to be carved out into slices, but also the Core Resources such as the Transport networks that connect Site, Edge and Core Clouds, and the Orchestration layer as well need to be sliced up. This provides for a scenario where the E2E network and other resources are abstracted for slicing into slices that carve up the shared physical infrastructures whose architectures could be multiple instances of varied combinations of what we know to be these resources, into a further varied architectures of logical resources grouped together as slices. This is an important point to understand in order to get a holistic view of a Many to many mapping of logical slices to actual physical infrastructure blocks of varied resources which are physical.
The physical infrastructure should project (and solutions need to be offered here) an abstraction and allocation strategy layer to the Network Slicing layer above this strategy layer to project actual physical resources and APIs to actually carve these physical resources and group them into network slices with their components in place for service delivery.
With regard to security, the strata where the physical components of varied architectures reside, may be
combined to form a logical network slice, hence the security aspects and requirements for each of the physical pieces put together for the logical network slice may be different but need to be managed as one single whole security strategy for the said network slice.
In summary there are many more issues and design roadblocks that may be faced in the future and as
these problems crop up suitable solutions need to be developed and implemented.
This paper presented a survey of the 5G network architecture and its important components. Most of the
discussion was focused on the Next-Generation RAN (NG-RAN) and the Next-Generation Core (NGC) components. A discussion on research and implementation challenges in realizing 5G network systems was also presented.
Acknowledgments: Part of this work was supported by a project funded by the Government of India’s Department of Telecommunications.
REFERENCES
[1] M. Agiwal, A. Roy, and N. Saxena, “Next Generation 5G Wireless Networks: A Comprehensive Survey,” IEEE Communications Surveys& Tutorials, vol. 18, no. 3, pp. 1617–1655, 2016.
[2] A. Checko, H. L. Christiansen, Y. Yan, L. Scolari, G. Kardaras, M. S. Berger, and L. Dittmann, “Cloud RAN for mobile networks: A technology overview,” IEEE Communications surveys & tutorials, vol. 17, no. 1, pp. 405–426, 2015.
[3] “ITU Y.3071: Data Aware Networking (Information Centric Networking) – Requirements and Capabilities,” Mar. 2018. [Online]. Available: http://www.itu.int/rec/T-REC-Y.3071-201703-I/en
[4] 3GPP, “Feasibility Study on New Services and Markets Technology Enablers,” 3rd Generation Partnership Project (3GPP), Technical Specification (TS) 22.891, 2016, version 14.2.0. [Online]. Available: http://www.3gpp.org/ftp//Specs/archive/22_series/22.891
[5] J. Costa-Requena, J. L. Santos, V. F. Guasch, K. Ahokas, G. Premsankar, S. Luukkainen, O. L. Pérez, M. U. Itzazelaia, I. Ahmad, M. Liyanage et al., “SDN and NFV integration in generalized mobile network architecture,” in Proc. of European Conference on Networks and Communications (EuCNC). IEEE, 2015, pp. 154–158.
[6] RFC3588, “Diameter Base Protocol,” https://tools.ietf.org/html/rfc3588,
2016.
[7] 3GPP, “Feasibility Study on New Services and Markets Technology Enablers,” 3rd Generation Partnership Project (3GPP), Technical Specification (TS) 38.801, 03 2017, version 14.1.0.
[8] A. Jain, E. Lopez-Aguilera, and I. Demirkol, “Mobility management as a service for 5g networks,” arXiv preprint arXiv:1705.09101, 2017.
[9] S. Abdelwahab, B. Hamdaoui, M. Guizani, and T. Znati, “Network function virtualization in 5G,” IEEE Communications Magazine,vol. 54, no. 4, pp. 84–91, 2016.
[10] X.-F. Tao, Y.-Z. Hou, K.-D. Wang, H.-Y. He, and Y. J. Guo, “GPPbased soft base station designing and optimization,” Journal of Computer Science and Technology, vol. 28, no. 3, pp. 420–428, 2013.
[11] Z. Zhu, P. Gupta, Q. Wang, S. Kalyanaraman, Y. Lin, H. Franke, and S. Sarangi, “Virtual base station pool: towards a wireless network cloud for radio access networks,” in Proceedings of the 8th ACM international conference on computing frontiers. ACM, 2011, p. 34.
[12] Texas Instruments, Inc., “Creating cloud base stations with TI’s KeyStone multicore architecture,” 2011. [Online]. Available: http://www.ti.com/lit/wp/spry183/spry183.pdf
[13] M. Yang, Y. Li, D. Jin, L. Su, S. Ma, and L. Zeng, “OpenRAN: a software-defined ran architecture via virtualization,” in ACM SIGCOMM computer communication review, vol. 43, no. 4. ACM, 2013, pp. 549–550.
[14] A. Gudipati, D. Perry, L. E. Li, and S. Katti, “SoftRAN: Software defined radio access network,” in Proceedings of the second ACM SIGCOMM workshop on Hot topics in software defined networking. ACM, 2013, pp. 25–30.
[15] T. K. Forde, I. Macaluso, and L. E. Doyle, “Exclusive sharing & virtualization of the cellular network,” in IEEE Symposium on New Frontiers in Dynamic Spectrum Access Networks (DySPAN). IEEE, 2011, pp. 337–348.
[16] P. Demestichas, A. Georgakopoulos, D. Karvounas, K. Tsagkaris, V. Stavroulaki, J. Lu, C. Xiong, and J. Yao, “5G on the horizon: Key challenges for the radio-access network,” IEEE vehicular technology magazine, vol. 8, no. 3, pp. 47–53, 2013.
[17] K. Sundaresan, M. Y. Arslan, S. Singh, S. Rangarajan, and S. V. Krishnamurthy, “Fluidnet: A flexible cloud-based radio access network for small cells,” IEEE/ACM Transactions on Networking, vol. 24, no. 2, pp. 915–928, 2016.
[18] X. Wang, A. Alabbasi, and C. Cavdar, “Interplay of energy and bandwidth consumption in cran with optimal function split,” in Proc. of IEEE ICC, 2017, pp. 1–6.
[19] 3GPP, “NG-RAN: Architecture description,” 3rd Generation Partnership Project (3GPP), Technical
Specification(TS) 38.401, 06 2018, version 15.1.0. [Online]. Available: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3219
[20] ——, “Summary of RAN3 status on CU-DU split Option 2 and Option 3, and questions/issues for RAN2,” 3rd Generation Partnership Project (3GPP), Technical document (Tdoc) R2-1700637, 01 2017, r2-1700637. [Online]. Available: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3219
[21] I. Giannoulakis, E. Kafetzakis, G. Xylouris, G. Gardikis, and A. Kourtis,“On the applications of efficient NFV management towards 5G networking,” in 5G for Ubiquitous Connectivity (5GU), 2014 1st International Conference on. IEEE, 2014, pp. 1–5.
[22] H. Hawilo, A. Shami, M. Mirahmadi, and R. Asal, “NFV: state of the art, challenges, and implementation in next generation mobile networks (vEPC),” IEEE Network, vol. 28, no. 6, pp. 18–26, 2014.
[23] 3GPP, “Security architecture and procedures for 5G System,” 3rd Generation Partnership Project
(3GPP), Technical Specification (TS) 33.501, 06 2018, version 14.2.0. [Online]. Available: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3169
[24] ——, “5G System; Access and Mobility Management Services; Stage 3,” 3rd Generation Partnership Project (3GPP), Tech. Rep. 29.518, 2018, version 15.2.0. [Online]. Available:https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3339
[25] ——, “System Architecture for the 5G System,” 3rd Generation Partnership Project (3GPP), Technical
Specification (TS) 23.501, 12 2017, version 14.2.0. [Online]. Available: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3144
[26] ——, “Procedures for the 5G System,” 3rd Generation Partnership Project (3GPP), Tech. Rep. 23.502, 12 2017, version 15.2.0. [Online]. Available:
https://portal.3gpp.org/desktopmodules/ Specifications/SpecificationDetails.aspx?specificationId=3145
[27] ——, “5G System; Session Management Event Exposure Service; Stage 3,” 3rd Generation Partnership
Project (3GPP), Tech. Rep. 29.508, 06 2018, version 15.2.0. [Online]. Available: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3351
[28] ——, “5G System; Access and Mobility Policy Control Service; Stage 3,” 3rd Generation Partnership Project (3GPP), Technical Specification (TS) 29.507, 06 2018, version 14.2.0. [Online]. Available: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3350
[29] ——, “5G System; Usage of the Unified Data Repository services for Subscription Data; Stage 3,” 3rd Generation Partnership Project (3GPP), Technical Specification (TS) 29.505, 06 2018, version 14.2.0. [Online]. Available: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3406
[30] ——, “5G System; Usage of the Unified Data Repository Service for Policy Data, Application Data and Structured Data for Exposure; Stage 3,” 3rd Generation Partnership Project (3GPP), Technical Specification (TS) 29.519, 06 2018, version 14.2.0. [Online]. Available: https://portal.3gpp.org/desktopmodules/ Specifications/SpecificationDetails.aspx?specificationId=3357
[31] R. El Hattachi and J. Erfanian, “Ngmn 5g white paper,” NGMN Alliance, February, 2015.
[32] J. Ordonez-Lucena, P. Ameigeiras, D. Lopez, J. J. Ramos-Munoz, J. Lorca, and J. Folgueira, “Network slicing for 5G with SDN/NFV: concepts, architectures and challenges,” arXiv preprint arXiv:1703.04676, 2017.
[33] “Network Functions Virtualisation – An Introduction, Benefits, Enablers, Challenges & Call for Action,” SDN and OpenFlow World Congress, Darmstadt-Germany, 10 2012. [Online]. Available: https://portal.etsi.org/nfv/nfv_white_paper.pdf
[34] Harrison J. Son and Chris Yoo, “E2E Network Slicing – Key 5G technology”,
https://www.netmanias.com/en/?m=view&id=blog&no=8325,