



The recent research studies on the internet-of-things (IoT) predict that the conventional IoT system without cognition will just be a burden on existing network infrastructure. In this article, we present a comprehensive survey on the recent research advancements in cognitive radio (CR)-based IoT (CR-IoT) framework. First, we provide a detailed discussion on the need to employ CR framework for IoT. Towards this end, we discuss in detail the challenges associated with the conventional IoT paradigm on the communication technology. This also includes several interdisciplinary requirements, such as technical challenges, security, hardware, standard, and business challenges that are the key factors for the deployment of CR-IoT systems. Next, integration of emerging techniques such as blockchain and machine learning with CR-IoT, and the associated advantages are discussed. Finally, we brief on the research challenges and future research directions in a CR-based IoT system.
The concept of Internet-of-Things (IoT) has captured the attention of research community with a vision of connecting physical objects over the internet at an unprecedented rate [1]. This network of physical objects is an interconnected web of smart devices, sensors, and other individual nodes, through which data can be collected. The accumulated data in its raw form is transmitted over the internet to be analyzed and processed to ï¬nd certain patterns or trends [2]. For instance, considering the present global situation of COVID-19 outbreak, inclusion of an integrated digital disease surveillance system may be crucial to control the growth of this pandemic [3]. Motivated by several such important applications, IoT is gaining global attention and becoming increasingly available for predicting, preventing and monitoring emerging infectious diseases. State-of-the-art IoT-enabled health monitoring systems [4] provide real-time surveillance through the use of wearable health-monitoring devices [5], cloud-based remote health testing [6], and artiï¬cial intelligence (AI) [7]. Therefore, IoT based smart disease surveillance systems have the potential to prove to be a major breakthrough [8].
Eï¬cient utilization of data handling techniques based on IoT and other new technologies could help in the prediction and early recognition of outbreaks, which can be used to prevent the spread of infectious diseases [9]. Smart disease surveillance systems based on IoT would provide simultaneous reporting and monitoring, end-to-end connectivity and aï¬ordability, data assortment and analysis, tracking and alerts, as well as options for remote medical assistance to be adopted, to detect and control infectious disease outbreaks in aï¬ected countries [10]. The current situation acts as one of the recent applications where advanced health care system can be developed by an advanced IoT-based system. Hence, the deployment of IoT systems not only provides continuous data assortment and analysis but also provides signiï¬cant savings and revenues in many areas, such as monitoring and maintaining solutions [11]. This has forced businesses to adopt diï¬erent strategies to cope with this exponential growth and the challenges associated with them, such as allocating suï¬cient spectrum bands in IoT applications [12, 13].
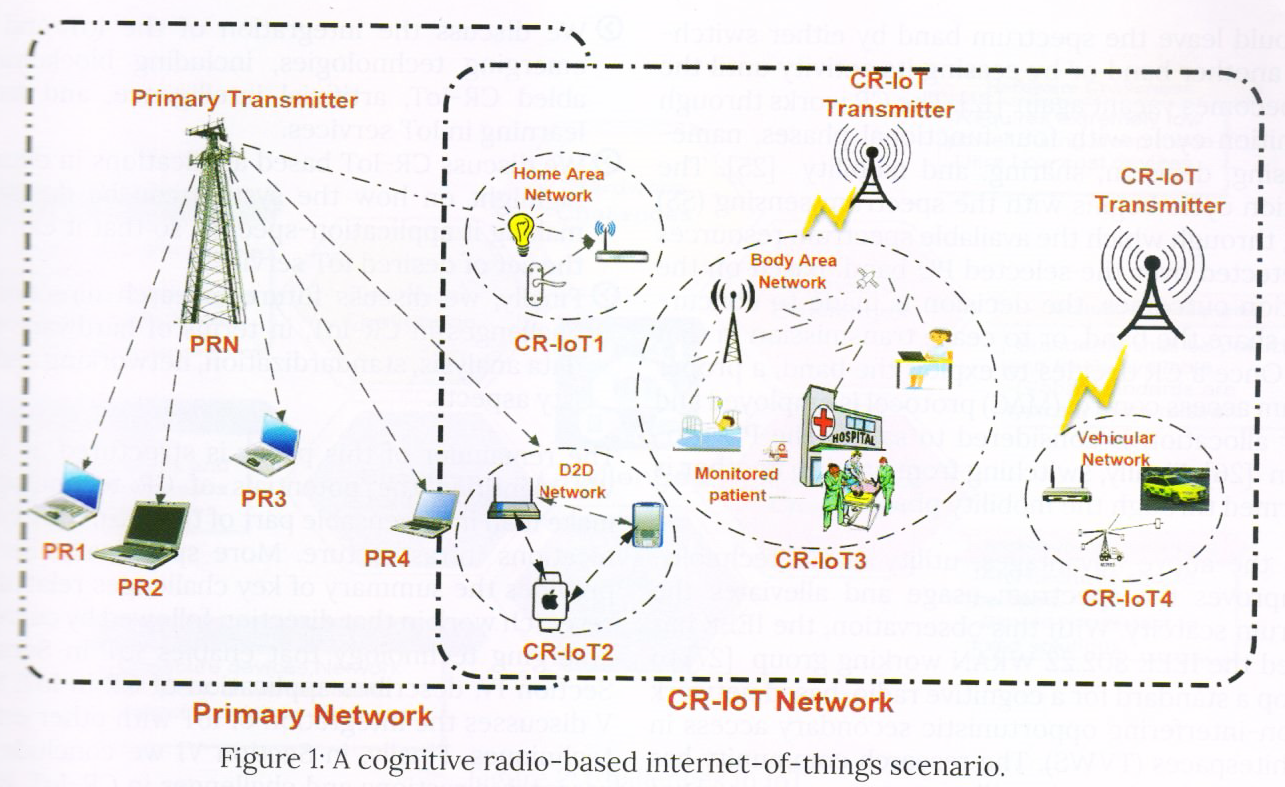
Figure 1: A cognitive radio-based internet-of-things scenario.
Despite its advantages, an IoT system without a brain is not enough to bring the expected convenient and comfortable life to humans. This observation has motivated to the recent development of a new paradigm called as the cognitive internet-of-things (CIoT) [14], which integrates the operational process of human cognition into the IoT system design. The CIoT paradigm also facilitates systematic developments in the key enabling techniques for the fundamental cognitive tasks involved in its research and development. The cognitive management framework also empowers the IoT towards a better supported sustainable smart city development, where cognition mainly refers to the autonomic selection of the most relevant objects for the given application – a feature which is not present in the conventional IoT. In [14], CIoT is viewed as the current IoT integrated with cognitive and cooperative mechanisms to promote performance and achieve intelligence.
A related topic is the concept of cognitive radio (CR) networks (CRN) – which was ï¬rst proposed by Mitola in 1999 [15], and revisited by Haykin in 2005 from a signal processing perspective [16]. Since then, research on CRN has been one of the actively studied topics in the ï¬eld of wireless communications. One common point in the ï¬elds of CIoT and CRN is that both of them beneï¬t from the recent advances in cognitive sciences [14]. However, the diï¬erences between CIoT and CRN are much more than the commonalities, which are listed next. The fundamental application of CRN is well-known, which is its potential as a promising paradigm to improve the utilization of radio electromagnetic spectrum, by allowing unlicensed radios to opportunistically access the idle spectrum licensed to the primary radios [17]. Therefore, CRN is essentially a radio system with the objective to improve the wireless network throughput. On the other hand, CIoT generally consists of (massive) heterogeneous general objects, not just radios, with various objectives designed for diï¬erent applications. Recently, the adaptation of CRN in IoT was presented in [18], which showed equivalent or better performance than currently used networks such as Wi-Fi, WiMax and Bluetooth [19]. An architecture of a CR-enabled IoT network, that coexists geographically with several primary user (PU) networks, is shown in Figure 1. As depicted, the CR-IoT network can be home area networks, body area networks, or vehicular networks, which utilize IoT functionalities. The PUs are licensed to transmit over a set of orthogonal non-overlapping channels, to their dedicated receivers. The CR-IoT devices periodically scan the vacant PU spectrum in order to access them opportunistically. Therefore, CR is considered as key IoT enabling technology, and its integration with future IoT architectures and services is expected to empower the IoT paradigm.
The need for an implementation of a CR-IoT network is also motivated by the need for an optimal usage of scarce spectrum resource by opportunistic approaches for radio frequency (RF) spectrum, which is one of the main challenges at hand [20]. The recent, unprecedented increase of wireless communication systems, applications and their users, limits the spectrum resources and connectivity between the interconnected objects. Therefore, the demand for smart devices that can manage and conï¬gure their transmission parameters based on the spectrum availability in spatio-temporal dimensions has remarkably increased. The CR technology is the best candidate to meet this requirement, due to its adaptability and intelligence to automatically detect available channels in a wireless spectrum. After that, it possesses the ability to change its transmission parameters to enable high data rate, concurrent communications, and also facilitates in improving the radio operating behavior [21]. In particular, new spectrum resources can be gained by allowing non-licensed users – also called as CR users or secondary users (SU) – to share a licensee user – also called as the PU – frequency bands, such that PUs should be always protected from the interference caused by SUs. Therefore, CR users must posses an additional feature that enables protection of the PUs to be of higher priority over any other own interest. The main beneï¬ts of CR systems for IoT devices would be to [19]
There are three paradigms or schemes by which a CR/SU can share the spectrum band owned by a PU, namely, overlay [22], underlay [23] and interweave [24]. For overlay and underlay schemes, a CR can coexist with the PU without interference or with a predeï¬ned, minimum interference. In the underlay scheme, the transmission power of the CR should be within a maximum limit, while there is no such constraint in the overlay scheme. However, the CR should have a full knowledge about the signal of PU, so that it can generate an orthogonal signal to the PU’s signal to eliminate/control interference. In the interweave scheme, a CR is allowed to transmit if and only if a PU is not utilizing its spectrum band. When and if the PU resumes its activity, the SU should leave the spectrum band by either switching to another band or by ceasing its activity until the band becomes vacant again [12]. The CR works through a cognition cycle with four functional phases, namely sensing, decision, sharing, and mobility [25]. The cognition cycle begins with the spectrum sensing (SS) phase, through which the available spectrum resources are detected over the selected PU band. Based on the detection outcomes, the decision is made to concurrently share the band, or to cease transmission in that band. Once a CR decides to exploit the band, a proper medium access control (MAC) protocol is employed and power allocation is considered to satisfy the PU protection [26]. Finally, switching from band to another is performed through the mobility phase.
Given the above advantages, utility of CR technology improves the spectrum usage and alleviates the spectrum scarcity. With this observation, the IEEE has created the IEEE 802.22 WRAN working group [27] to develop a standard for a cognitive radio-based network for non-interfering opportunistic secondary access in TV whitespaces (TVWS). The research community has adopted CR for dynamic radio spectrum management to enhance spectrum usage, e.g., in ISM bands and as SUs in unused TV bands. Moreover, several companies, such as Motorola, Philips, and Qualcomm, are now investing in the development of CR technology [28]. As a related sidenote, the European research cluster on the Internet-of-Things (IERC) has provided the roadmap on standardization for IoT technologies [29]. One of the IERC projects, namely RERUM [30] is working on adapting CR on the IoT devices. The focus is on investigating the adaptation of CR technology in smart objects to minimize wireless interference and ensure the always connected concept. The advanced capabilities of a CR include spectrum sensing, awareness of its surroundings, learning and self-adapting allow to maintain eï¬cient communication in an opportunistic manner. Overall, the cognitive and self-organization capabilities, and reconï¬gurable nature of CR along with the advances brought about by CR technologies will drive and enable an eï¬cient IoT. In view of this, we discuss the challenges faced by IoT technologies and provide an extensive survey on the approaches to overcome these challenges by integrating CR with IoT systems. Later, we elaborate on several IoT applications that use CRs. Finally, we discuss open research challenges, recent advancements, ongoing and future research directions in CR-IoT systems. The outline of the contributions of this paper relative to the recent literature in the ï¬eld can be summarized as:
The remainder of this paper is structured as follows. We identiï¬ed the potentials of CR technology that make it an indispensable part of the future IoT communications infrastructure. More speciï¬cally, Section 2 provides the summary of key challenges related to IoT research work in that direction followed by current and emerging technology that enables IoT in Section 3. Section 4, describes application of CR in IoT. Section 5 discuss the integration of IOT with other emerging techniques . Finally in Section 6 we conclude future research directions and challenges in CR-IoT, in terms of hardware design, data analysis, standardization, networking and security aspects.
Figure 2: Challenges in IoT.
The IoT paradigm enables the regular physical objects to be smart by exploiting its underlying technologies such as ubiquitous and pervasive computing, embedded devices, communications and sensor networks, IP and applications. However, IoT by itself lacks technology and standards that integrate the virtual world and the real physical world in a uniï¬ed framework. In the following, we shall shed light on some of the design issues and challenges in IoT – as shown in Figure 2, which are currently hindering IoT to achieve its fullest potential [31]. Later, we argue that CR can be a promising enabler technology for IoT as it can help in addressing many of these following challenges.
A. Technical Challenges
Its not an easy mission to successfully establish a smooth functionality of IoT systems as a standalone solution or part of existing systems since, there are many technological challenges, which include security, connectivity, compatibility and longevity, standards and intelligent analysis and actions.
a) Security: The main idea behind the working principle of IoT has already put forth a serious security concern, which has drawn the attention of prominent tech ï¬rms and government agencies across the globe [32]. The hacking of baby monitors, smart fridges, thermostats, drug infusion pumps, cameras and even the radio in a car are signifying a security nightmare being caused by the future of IoT [33]. New nodes being added to networks and the internet will provide malicious actors with innumerable attack vectors and possibilities to carry out their evil deeds, especially since a considerable number of them suï¬er from security holes. The more important shift in security will come from the fact that IoT will become more ingrained in our lives. Concerns will no longer be limited to the protection of sensitive information and assets. Our very lives and health can become the target of IoT hack attacks [34].
b) Connectivity: Connecting many devices will be one of the biggest challenges of the future of IoT, and it will defy the very structure of current communication models and the underlying technologies [35]. At present, we rely on a centralized server/client paradigm to authenticate, authorize and connect diï¬erent nodes in a network. Such a model is suï¬cient for current IoT ecosystems, where tens, hundreds or even thousands of devices are involved [36]. But when networks grow to join billions and hundreds of billions of devices, centralized systems will turn into a bottleneck. Such systems will require huge investments and spending in maintaining cloud servers that can handle such large amounts of information exchange, and the entire system can go down if the server becomes unavailable. The future of IoT will very much have to depend on decentralization in terms of networks. Part of it can become possible by moving some of the tasks to the edge, such as using fog computing models where smart devices such as IoT hubs take charge of mission-critical operations and cloud servers take on data gathering and analytic responsibilities [37]. Other solutions involve the use of peer-to-peer communications, where devices identify and authenticate each other directly and exchange information without the involvement of a broker. Networks will be created in meshes with no single point of failure. This model will have its own set of challenges, especially from a security perspective, but these challenges can be met with some of the emerging IoT technologies, such as blockchain [38].
c) Compatibility and Longevity: IoT is growing in diï¬erent directions, with diï¬erent technologies competing to become the standard. This will cause diï¬culties and require the deployment of extra hardware and software when connecting devices. Other compatibility issues stem from non-uniï¬ed cloud services, lack of standardized M2M protocols and diversities in ï¬rmware and operating systems among IoT devices. Some of these technologies will eventually become obsolete in the next few years, eï¬ectively rendering the devices implementing them useless. This is especially important, since in contrast to generic computing devices which have a lifespan of a few years, IoT appliances (such as smart fridges or TVs) tend to remain in service for much longer, and should be able to function even if their manufacturer goes out of service.
d) Intelligent Analysis and Actions: The last stage in IoT implementation is extracting insights from data for analysis, where analysis is driven by cognitive technologies and the accompanying models that facilitate the use of cognitive technologies. Unnecessary competition and deployment barriers in markets, will block the migration of IoT systems to connect as many Things as possible.
B. Hardware challenges
Smart devices with enhanced inter-device communication will lead to smart systems with high degrees of intelligence [39]. Its autonomy enables a rapid deployment of IoT applications and creation of new services. Therefore, hardware research is focusing on designing wireless identiï¬able systems with low size, low cost and yet, suï¬cient functionality. As the bandwidth of IoT terminals could vary from kbps to Mbps from sensing [40] simple value to video stream, requirements on hardware are diverging. However, two requirements have been nevertheless the essentials. First is the extremely low power consumption in sleep mode and the other is ultra low cost. Suppose the sleeping time over active time is one million, the leakage power of an IoT terminal shall at least be one million time less than that of active. It is so far impossible when an IoT terminal is sleeping and receiving RF signals. It will be even diï¬cult when using advanced CMOS silicon with relatively more leakage power. Hardware and protocol design are the ï¬rst hardware challenges of IoT [41]. The cost, performance and power are few factors which are interdependent. The cost of an IoT terminal must be ultra-low. However, so far, there is no low-cost positioning solution for IoT, especially the positioning precision of a short-range IoT terminal must be high. Low active power is also a challenge for low-cost terminal [42]. Traditionally, low cost equals to lower performance or longer process latency. Longer processing latency ends up to higher energy consumption. As the spectrum resource is very limited at the lower part in L band, IoT uses higher RF such as the frequency bands higher than 5 GHz. To use very narrow band with strong power neighbors, the cost of passive component will not be low and that will deï¬nitely be a potential challenge in the future.
C. Architecture Challenges
In IoT, data integration over diï¬erent environments are challenging and will be supported by modular interoperable components. Infrastructure solutions will require systems to combine volumes of data from various sources and determine relevant features to interpret the data, show their relationships, compare data to historical useful information, and support decision-making. Below are some of the architecture challenges faced by IoT.
e) Lack of Standardization: One of the many signiï¬cant issues faced by an IoT Architecture is the variety of languages, protocols, and standards. Also, the lack of agreement on which it works. IoT architecture does not have a single platform of standardization. It is changed due to the diï¬erence of connected things. The hardware and software components related to the IoT should also be standardized. Having a standardized application programming interface (APIs) and software service enables easy migration across systems.
f) Connectivity: Connectivity is an important component of IoT architecture because it plays a crucial role in transporting data from the sensors [43]. Furthermore, it also transmits instructions to the actuators. In the context of IoT, connectivity can be examined at various levels from the frequency bands at the physical layer to MAC protocols at the link layer, transport protocols at the transport layer, network protocols, and mobility at the network layer and application protocols at the application layer.
g) Interoperability This is one of the major challenges of an IoT architecture. IoT applications oï¬er value to users by combining data sets from various IoT devices. They do this in order to generate interconnected and complex business rules [44]. These business rules further actuate IoT devices to automate the process. Eï¬ective business rules generation requires interoperability, which is not an easy task because of multiple vendor problems and legacy system issues.
h) Mobility: Mobility is a common challenge in IoT architecture, where the devices have to move a lot. Therefore, the devices change their IP addresses and networks frequently based on their locations. Since there are a large number of devices and a massive amount of data transmission which leads to network disturbance and data loss, single reference architecture cannot be a blueprint for all applications. Heterogeneous reference architectures have to coexist in IoT. Architectures should be open, standardized and it should not restrict users to use ï¬xed, end-to-end solutions. IoT architectures should be ï¬exible to cater for cases such as identiï¬cation (RFID, tags), intelligent devices, and smart objects (hardware and software solutions).
D. Privacy and Security Challenges
Cybersecurity is one of the more pressing challenges when it comes to IoT. With the nature of this system being widely connected, it leaves vulnerabilities for hackers to take advantage. As the basic principle of IoT involves connecting devices, it makes everything addressable and locatable which in turn makes our life easier [45]. However, making everything connected to internet opens the door for hackers. Without proper conï¬dence about privacy and security, user will not be attracted towards IoT [46]. So, it must have a strong infrastructure dealing with security. Below are some of the issues that IoT might face.
Standards play an important role in forming the IoT ecosystem. A standard is essential to allow all actors to equally access and use [52]. Developments and coordination of standards and proposals will promote eï¬cient development of IoT infrastructures and applications, services, and devices. In general, standards developed by cooperated multi-parties, and the information models and protocols in the standards shall be open. The standard development process shall also be open to all participants, and the resulting standards shall be publicly and freely available. In today’s network world, global standards are typically more relevant than any local agreements.
The growing advancement in sensor technology with respect to range, sensitivity, and resolution in terms of speed and coverage, led to the advancement of IoT implementation. Accenture’s latest Industrial IoT trend study conï¬rms that 60% of the companies are already engaged in IoT projects, more than 30% are at an early stage of deployment, and 69% of these companies’ IoT initiatives are focused on reducing operational cost [53]. This advancement in technological initiatives can help businesses generate insight and provide valued services to their customers, at a reduced operational cost. On the other hand, despite the availability of resources and advancements in key IOT components such as sensors and networks, many companies have not been able to make substantial beneï¬ts out of their IoT project. According to a data released by Cisco, 74% of surveyed organizations have failed with their IoT initiatives [54]. This is mainly because there are several human factors involved in IoT implementation, beyond the functional elements of sensors and networks. An eï¬ective collaboration and integration among all the components of IoT, along with creating a culture of technology within the organization is required to succeed. But in doing so, many companies face critical challenges related to security network investment and data analysis. Moreover, most of the companies are often prepared to handle sensors and data analytics, whereas, they fail to bring the same level of expertise into network investment, system integration, and security. Besides, on the occasion of IoT World Forum 2017, Cisco released a survey that highlights a perception gap between the IT executives and business executives [55]. About 35% of surveyed IT executives perceived their IoT project as successful, while only 15% of business executives believe that the initiative was a success. This percentage gap highlights a rift between technology and value delivered. While the IT department is sure of bringing the technology required for a successful IoT project, it is the lack of value delivered, which makes business executives consider the IoT project to be unsuccessful. Capturing invaluable data that lead to false insight could also be the reason many business executives consider their IoT projects unsuccessful.
In section 2, we discussed some of the design issues and challenges that are currently hindering the realization of IoT, such as technical challenges, heterogenety, low cost low power design, interoperability, connectivity, compatibility etc. which were categorized as technical, architectural, hardware, security, and business challenges. Current ï¬xed spectrum utilization policies have resulted in ineï¬cient utilization of spectrum [18]. To overcome this situation, CRNs opportunistically search for available spectrum bands by dynamically changing transmitter parameters based on interaction with the environment. Each node has the characteristic of fast switching with simultaneous transmissions in addition to channel probing and channel state learning. Dynamic spectrum access (DSA) capability enables a CR user to adapt to varying network conditions. A CR user is allowed to use the spectrum with guaranteed protection to the legitimate user, or the PU. With the ongoing development in CRNs and IoT, it is envisioned that CR-based IoT frameworks may become necessary requirements in the future. The IoT objects would be equipped with cognition in order to learn, think, and make decisions through understanding of both social and physical worlds [46]. Additional requirements include intelligent decision making, perception action cycle, massive data analytics, on-demand service provisioning, semantic derivation, and knowledge discovery. Therefore, a CR-based IoT is a foreseeable need in the future, which may be due to the following reasons.
In this section, we present some of the potential applications of IoT that can beneï¬t from its integration with CRNs. Table I summarizes the state-of-art literature on applications of CR-IoT in terms of technical parameters relevant to IoT and CR technologies.
| CR-IoT for smart grids/smart metering | ||||
| Reference | Technology Parameter | IoT Context | CR Use | Remarks |
| [60] | Energy harvesting (EH) approaches | To increase the lifetime of wireless devices. | To overcome harsh channel conditions and spectrum scarcity problems in its network architecture. | The proposed network is investigated in terms of general operation node and network architecture aspects. |
| [61] | NB-IoT is proposed to provide secure and reliable communications among different components in a power system. | Four typical communication scenarios such as rural area, bad urban area, typical urban area, and hilly terrain area are examined. | Conventional communication technologies such as ZigBee, WiMax, LPWAN, and LoRa are investigated. | NB-IoT framework performs well in the presence of LOS paths and the performance can be improved with the subcarrier interleaving technique. |
| CR-IoT for smart homes | ||||
| [62] | Novel concept of introducing the CR in the smart home environment. | IoT-based smart home that facilitates the CR network for efficient spectrum sensing and management is investigated. | A prototype for implementing CR-based communication for smart homes was developed using NI USRP and LabView. | Prototype implementation of smart home using SDRs. |
| [63] | IoT-enabled home automation and security systems using passive infrared motion sensors, temperature sensors, smoke sensors, and web cameras for security surveillance. | A framework to build a low-cost smart home security system using affordable components such as Arduino-compatible, Elegoo Mega 2560 micro-controller board with Raspberry Pi and RF signals. | Low-cost, RF-based transceiver communication is utilized to create an IoT-enabled smart home security system. | An architecture for a cost-effective smart door sensor that will inform a user through an Android application, of door open events in a house or office environment is proposed. |
| CR-IoT for health care and medical applications | ||||
| [64] | A CR system is proposed for e-healthapplications in a hospital environment, which protects the medical devices from harmful interference by adapting the transmit power of wireless devices based on electromagnetic interference (EMI) constraints. | Two e-health applications, namely, tele-medicine and a hospital information system are considered. | The cognitive capability of the system arises due to its EMI awareness to control the wireless access parameters in order to achieve the desired QoS differentiation among different users/applications. | Admission control algorithm, and transmit power control methods are used to limit the number of secondary users in the system. This improves the delay and loss probability of the CR system. |
| [65] | ECC-based smart-health care system. | To monitor and analyze the physical health of users using cognitive computing. | It adjusts the computing resource allocation of the whole edge computing network according to the health-risk grade of each user. | Optimizes the computing resources, improves the survival rates of patients in a sudden emergency. |
| CR-IoT for public safety and disaster management | ||||
| [66] | Explored the potentials of CR technology in future public safety communication infrastructure. | Public safety operation embracing SG and IoT to periodically send the sensing information to that cloud using LTE. | Introduces a case study and shows how CR technology can be used to enhance the experience of the first responder by improving their communication capabilities. | CR technology to enhance the emergency service by improving their communication capabilities. |
| [67] | The operational and technical requirements for DRN is explored for emergency response organizations and personnel. | Disaster Response scenario for an area after communication is destroyed, including UAV-based interoperable systems. | Assessed the potential for CR technology in DRN solutions. | CR technologies can be utilized in future mission-critical situations. |
| CR-IoT for vehicular networks | ||||
| [68] | A secured and efficient communication scheme for a decentralized CR-based IoV (CIoV) network is proposed. | The performance of CIoV is evaluated in terms of packet delivery, packet loss ratio, end-to-end delay, and throughput, using NS-2. | The RSU senses the spectrum using an energy detection method. | The CR-based approach of CIoV outperforms the existing schemes and significantly enhances the performance of the underlying network. |
| [69] | Proposed a novel CR-assisted vehicular network (CRAVNET) framework which empowers CR-enabled vehicles to make opportunistic usage of licensed spectrum on the highways. | IoT and vehicular technology are combined to form IoV to empower intelligent transportation systems. | A novel cooperative three-state spectrum sensing and allocation model is proposed. | The proposed model can significantly improve the performance of a cooperative spectrum sensing, and provide vehicles with additional spectrum opportunities. |
| CR-IoT for military applications | ||||
| [70] | Different IoT applications and methodologies, protocols and methods of implementation for military activities. | Application, protocol and security aspects of IoT in military operations. | Not used. | IoT applications, methodologies, protocols and methods of implementation used for military activities are presented. |
| [71] | Exploits smart city IoT capabilities in military operations. | Security challenges when IoT is utilized for military purpose, mitigating those challenges, and how IoT sensor information can be provided to the military units in an operation are discussed. | Not used. | Work performed by the NATO IST147 Military Applications of Internet of Things group is presented. |
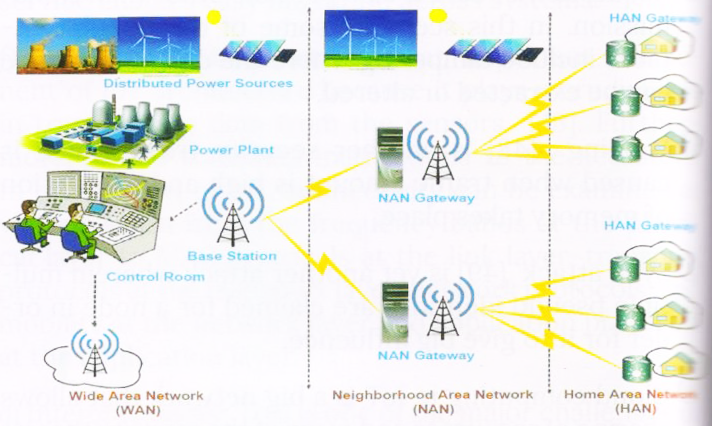
Figure 3: A CR-based, IoT-enabled smart grid scenario.
1) Smart Grids and Smart Metering: The centralized management of the electric grid has experienced a paradigm shift towards the smart grid (SG). It enables the two way communication, which connects the consumer side and the utility companies [72]. This paradigm provides an eï¬cient management and control of the grid in a better way by monitoring of demand and supply in real time. Hence, SG adds new services to the customers, in which they can adjust their energy consumption according to the demand and supply balance. The SG can beneï¬t from the application of the IoT technology since the IoT enables smart monitoring of the environment, eï¬cient management of resources by smart meters, home gateways, smart plugs and connected appliances which provides eï¬ciency in energy production and consumption [60]. Autonomous monitoring, diagnosis and control, and eï¬cient operation of the power equipment for the power generation, and distribution require monitoring and actuating devices [73]. Hence, the inclusion of the IoT in SG is important. This will increase the utilization of information and communication technologies in the SG and provide eï¬ective management of power grid system [61]. One major drawback here is the transfer of large volumes of data from a number of meters/devices in a limited spectrum bandwidth without interference to long distances. Current wireless techniques have issues regarding this. Wired techniques such as DSL and optical ï¬ber, and wireless techniques such as cellular can overcome these problems, but need huge expenditures for cable/ï¬ber installation or spectrum purchase. Therefore, CRNs as a viable solution for this issue [74]. An IoT-enabled SG architecture with cognitive radio can be seen in Figure 3, which shows that the elements of the SG such as energy harvesting cognitive radio nodes which communicate over the Internet. The condition of power grid elements, their energy production, the consumption of the energy are observed and measured via the IoT devices. The observations and measurements are sent over multiple hops to reach the internet gateway, to send them to remote areas for necessary actions to be taken in the IoT-enabled SG. Power consumption in industrial, commercial and residential sites can be monitored, and the power generated by renewable energy resources can be observed in real time via the Internet which increases accessibility.
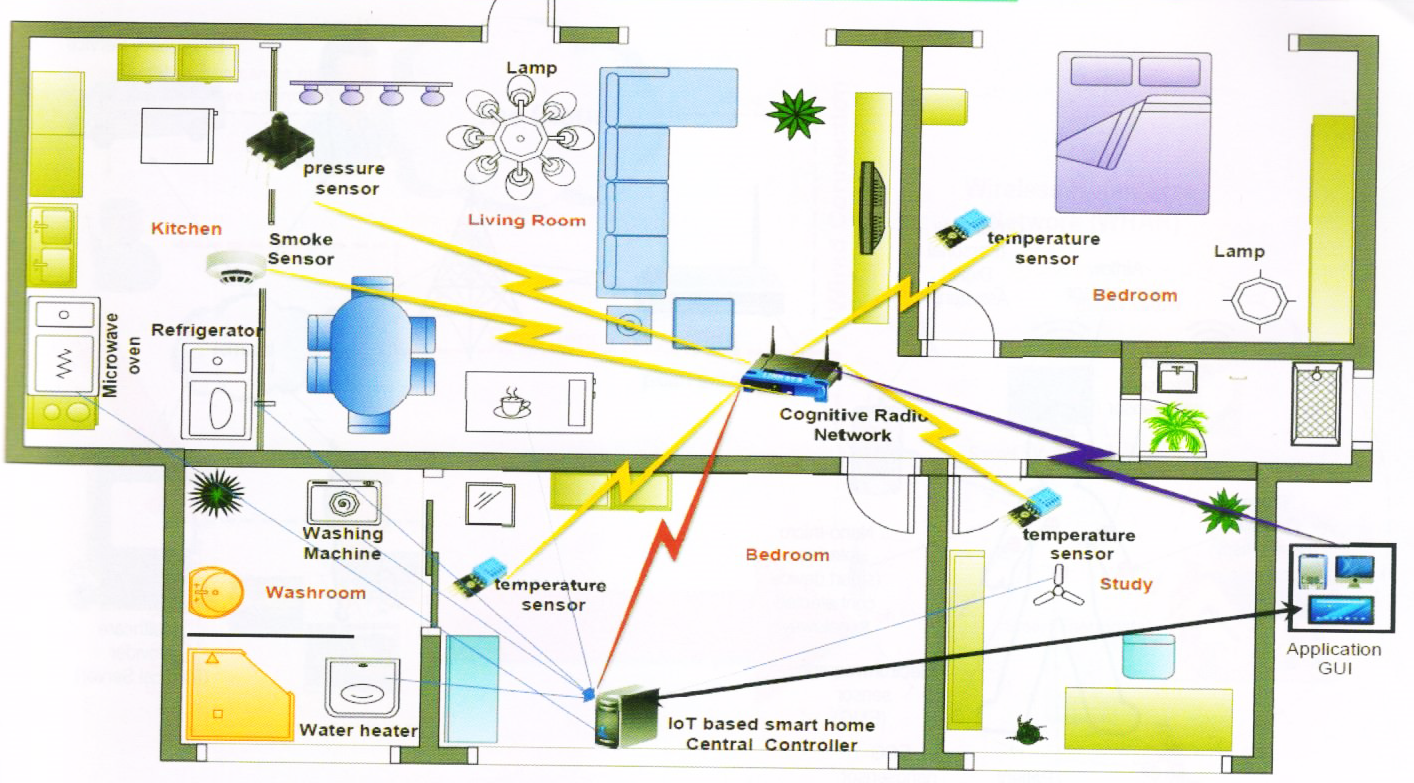
Figure 4: A CR-based, IoT-enabled smart home scenario.
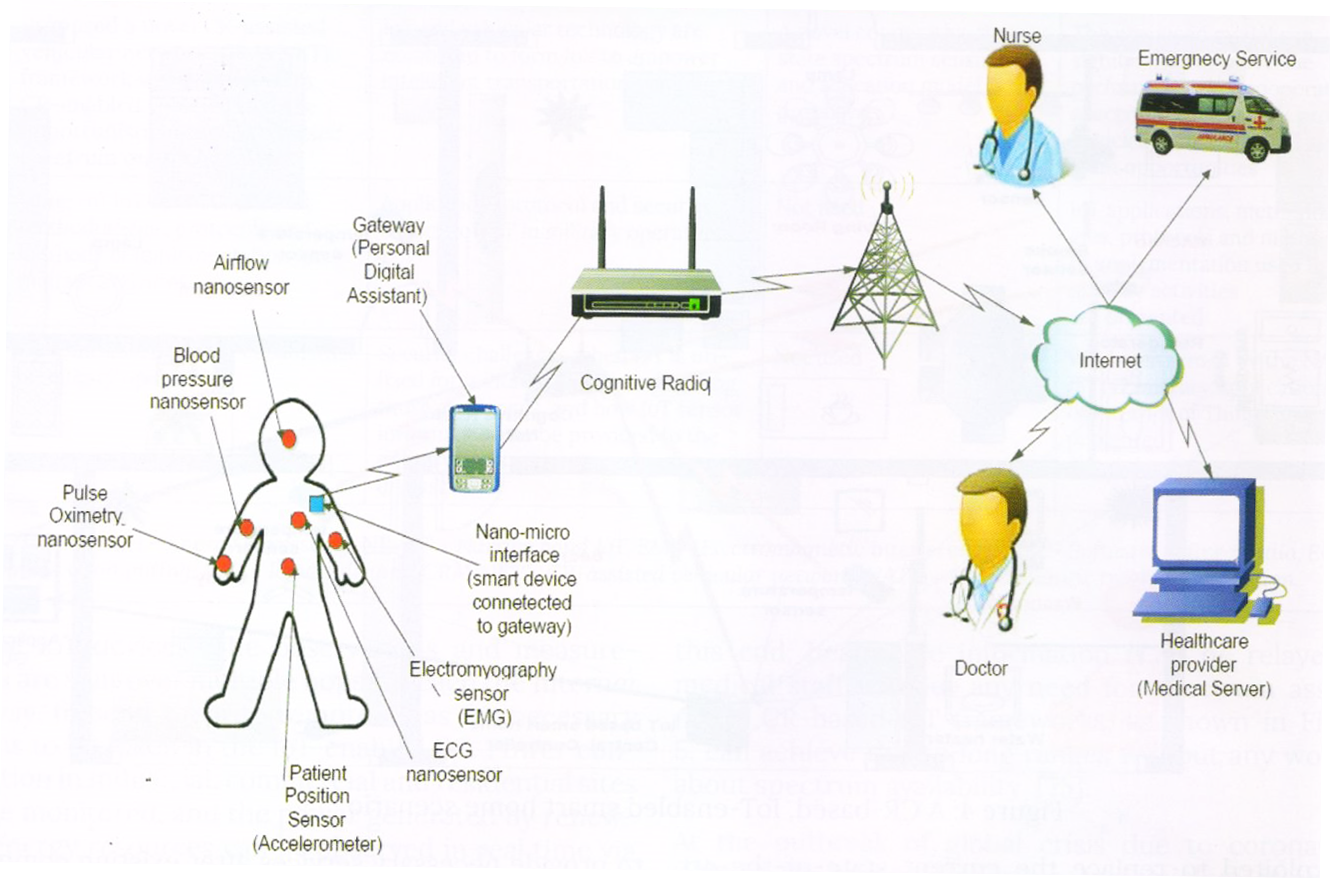
Figure 5: A CR-based, IoT-enabled remort health care monitoring system.
2) Smart Homes: Rapid growth of wireless technology prompted for the development of smart home which consist of a large number of self-organizing wireless smart devices like smart phones, wireless cameras, laptops, HDTV, smart meters and smart domestic appliances (see Figure 4). It is envisioned that with the evolution in technology, the era of IoT will be a necessity in the future. Homes will be incorporated with sensors/devices to perform everyday functions for improved quality of life. Home automation and home energy management are already present in the form of certain examples such as smart fridge and smart lights, respectively. These smart devices are equipped with small radio devices for monitoring and remote controlling. Some of these devices use short range unlicensed bands like ISM band, which is overloaded. Also, a large number of smart home devices tend to create inter-user interference while using these bands. The future smart homes will face spectrum shortage problem. The solution to these problems is incorporating a CRN. Additionally, switching from unlicensed ISM band to TVWS will reduce energy consumption [73].
3) Healthcare and Medical Applications: We have healthcare applications of IoT already in the practical domain. Smart sensors are deployed on and around a patient to monitor critical data such as temperature, blood pressure, glucose level, and others. With remote monitoring, medical staï¬ continuously observes the parameters. Wireless solutions are already there; however, it is urgent that smooth monitoring is ensured. Towards this end, healthcare information is to be relayed to medical staï¬ without any need for spectrum assignment. CR-based IoT frameworks, as shown in Figure 5, can achieve this to long ranges without any worries about spectrum availability [75].
At the outbreak of global crisis due to coronavirus (COVID-19), infectious disease epidemiology is another emerging ï¬eld of IoT based health care application which is rapidly gaining global attention and becoming increasingly available for predicting, preventing and monitoring emerging infectious diseases. State-of-the-art IoT-enabled health monitoring systems provide real-time surveillance through the use of wearable health-monitoring devices, cloud-based remote health testing, and artiï¬cial intelligence. The ubiquitous availability of smart technologies, as well as increased risks of infectious disease spread through the globalization and inter-connectivity in the world necessitates its use for predicting, preventing and controlling emerging infectious diseases [76]. IoT-enabled health monitoring in a global health care infrastructure would provide targeted information for health oï¬cials, and has the potential to improve eï¬orts to locate, contain, and prevent infectious diseases. It may help to quickly diagnose infected patients and accurately predict the possible spread of a disease to other locations utilizing travel data. Ultimately, an IoT based surveillance system might help reconstruct the progression of an outbreak and stabilize the economy of the source country rather than having to lock down major cities, borders and businesses.
4) Emergency Networks: Public safety agencies are increasingly using wireless communication technologies to monitor disaster conditions using video surveillance cameras and sensors. The increasing use of this setup has led to congestion in radio frequency channels allocated to the agency [19]. In order to address the aforementioned issue of optimum resource allocation during emergency response, CR-IoT technology could be exploited to replace the current state-of-the-art channel allocation protocols [67].
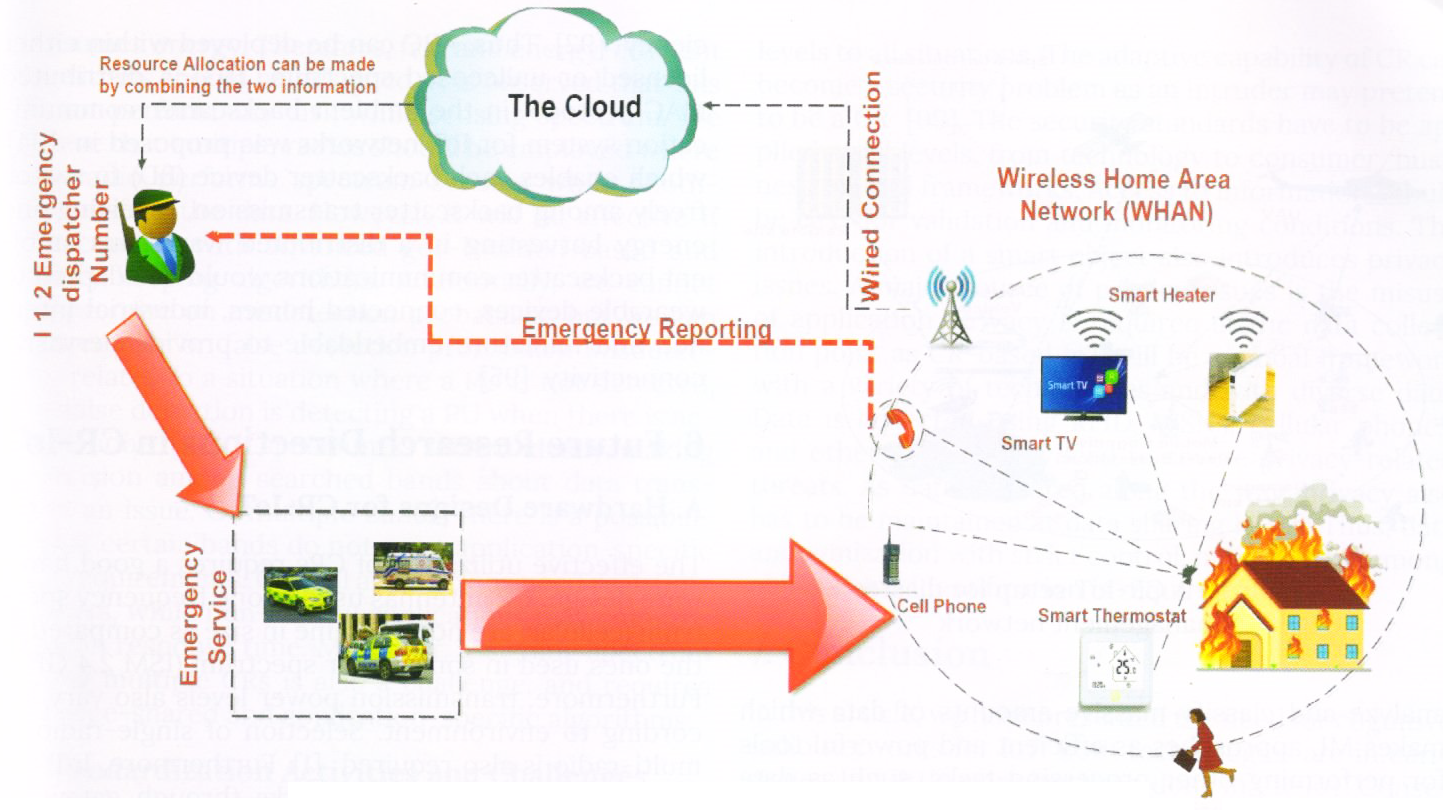
Figure 6: A CR-IoT setup for emergency network for public safety.
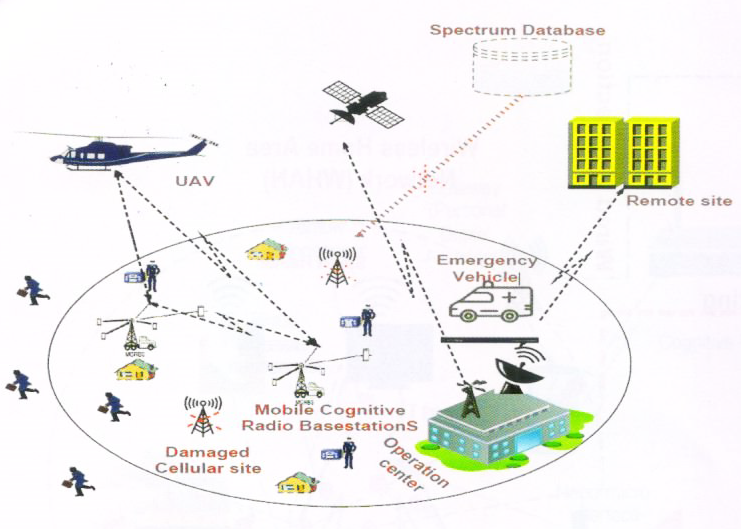
Figure 7: A CR-IoT setup for diaster management network.
When responding to an emergency situation, ï¬reï¬ghters, police oï¬cers or lifeguards can pull out information about the internal design of the building and have a knowledge about who is inside by identifying the personal computing devices – smart phones in particular – present in the house. Indoor sensors and smart meters can also help track the spreading of ï¬ames, identify the safest place to enter the house and identify all running appliances that may cause safety hazards. This example is depicted in Figure 6. The ï¬gure shows that indoor sensing information can be used by the 1 − 1 − 2 emergency service team to better assess the required resources attending the incident. As part of the SG and/or the IoT, this sensing information is periodically sent to the cloud using a variety of wireless communications networks such as LTE. The next generation IoT, WSNs, SG, and big data analytics stands as a major enabler to realize future intelligent infrastructures for enhanced disaster management. The widespread demand for data and the emergence of new services are inevitably leading to the so-called resource crisis. Hence, the evolution of the current centralized model of networked systems to new paradigms such as low power high data rate cognitive networks present a suitable path to counteract this crisis.
The CR-IoT scheme is also a potential candidate in disaster management for partially or fully destroyed network. It can be utilized in a disaster management network (DMN) which is a communication network that is rapidly deployed in the aftermath of a disaster, to provide necessary services after existing communications infrastructure has been damaged [67].
In Figure 7, a DMN is shown where non-governmental organization and emergency services perform their initial setup in an operation center. Static/mobile cognitive radio base stations (CRBSs) can be used to provide radio connectivity, with backend connectivity to the operation center in a multihop manner, or with unmanned aerial vehicles. The operation center can be connected to the internet via satellite/backhaul links or to other nearby base stations/disaster-sites through multihop CRN. In a disaster scenario, we consider the DMN as a SU and the existing/partially destroyed network a PU. Thus the DMN avoids harmful interference on the already existing systems. If the SU detects a PU in the course of operation, it reconï¬gures its operation in order to avoid causing interference. To assess damage and service requirements, emergency service personnel can carry auto-conï¬guring CR devices to aï¬ected areas immediately after the disaster. These CRs can carry out spectrum sensing [77] and use ad-hoc, multihop, and mesh networking techniques to relay information using delay-tolerant applications. Following initial assessment, mobile/static CRBSs can be used to extend connectivity and provide services to inaccessible regions, as shown in Figure 7. Thus, self organizing and dynamic spectrum management capabilities of CR-IoT nominate it as a strong candidate in disaster management network.
CR-IoT can also be applied for emergency networks, e.g. ambulance, ï¬re, police, and rescue, to provide a signiï¬cant amount of bandwidth to natural disasters that can cause a collapse of the communications infrastructure. This necessitates an operation in a CR environment to handle the expected huge amount of sensitive real-time data transmission [78, 67]. In Figure 7, we illustrate how the CR rapid deployment and interoperability between network units can provide connection to all communication units, when the communication is aï¬ected in disaster relief environments [78].
5) CR-IoT Venhicular Networks: Recently, trends are shifting toward less dependence on human beings, which has led us toward the internet-of-vehicles (IoV) paradigm where vehicle control is achieved through the integration of communications, controls, and embedded systems. The IoV system is expected to be an autonomous decision maker for traveling. Safe navigation may be possible in the future through information exchange from vehicles to vehicles, from sensors attached on vehicles, and through users’ intentions. The challenge in IoVs is the availability of spectrum for mobile vehicles, and CRN can be a good solution technology due to its long range and interference-free spectrum sensing [79].
6) Military Applications: The future of military combat is going high-tech, as scientists are in process to create an IoT for combat gear embedded with biometric wearables to help soldiers identify the enemy, perform better in battle, and access devices and weapons systems using speedy edge computing [71]. Towards this end, IoT serves as a potential candidate to bring a paradigm shift in military application development. By integrating systems of sensors, actuators, and control systems into existing military infrastructures, the military can become more eï¬cient and eï¬ective. Few areas for IoT military applications are listed below:
Integration of CR-IoT with other emerging technologies such as blockchain, artiï¬cial intelligence techniques, machine learning approaches, can make the IoT network smarter and more productive. Furthermore, it will be a new step towards creating next-generation wireless communication systems with additional capabilities such as robust security, autonomy, ï¬exibility, and intelligent architecture which are more energy eï¬cient. This section discusses the impact of adding blockchain, machine learning and ambient backscattering communication (ABC) techniques that support sustainable and independent communications to CR-based IoT systems.
7) Blockchain-Enabled CR-IoT System: The blockchain is deï¬ned as a tremendous, public, secure and decentralized datastore of ordered events, called blocks. Each block contains a timestamp and is linked to a previous block. The events can be updated by only a majority users [82]. Erasing information is not allowed. The datastore is owned by no one, controlled by users and not ruled by any trusted third party or central regulatory instance. In fact, trust is encoded in the protocol and maintained by the community of users. The work in [83] presented a comprehensive survey on blockchain, its types, features, structures, protocols, and the integration of blockchain and IoT systems. On the other hand, the survey in [84] focused on blockchain applications and challenges for real world applications. Adopting blockchain technology is a promising solution to improve system immunity against hacking activities. The blockchain prevents central point system failure and cyber attack which results in improving the security in IoT and CRNs. The blockchain protocols employ a two-key encryption system, i.e., public and private keys; therefore, robustness is added to the security of CRNs [82]. However, the use of blockchain in IoT security is limited and focused on the following areas: asymmetric and symmetric key management, trading of collected data, incontrovertible log of events, and management of access control to data [85]. The security issues related to IoT include authentication and authorization, ownership and identity relationships, governance of data and privacy [86]. Blockchain-based research has been used to tackle some of these issues. Such work is still in its infancy and worth investigating since introducing blockchain in IoT and CR systems shows a promising future in supporting secure data sharing and protecting privacy. On the other perspective, employing blockchain protocols in spectrum auction oï¬ers a decentralized validation which increases the accessibility of the CRNs and reduces the implementation complexity, since no central entity is required. In addition, blockchain-enabled spectrum access in CRN is a secure spectrum sharing approach where it provides an optimal collision-free method to access the spectrum opportunities.
8) Machine Learning-Enabled CR-IoT System: Machine learning (ML) approaches are artiï¬cial intelligence (AI) applications that establish mathematical models based on observations, i.e., training data, to predict or make decisions. ML approaches enable systems to automatically learn and improve from experience without being explicitly programmed. In other words, ML approaches enable computers or processors to automatically learn without human intervention and to select actions accordingly. ML approaches have a potential ability to analyze and classify massive amounts of data which makes ML approaches as eï¬cient and powerful tools for performing other processing tasks, such as data analysis, classiï¬cation [87], feature detection, feature extraction [88] and identiï¬cation [89]. Also, ML approaches improve the security and the data privacy for big data systems [90]. In addition to the aforementioned advantages, ML approaches can apply complex techniques in a simple way, and provide accurate results of identifying the targets. Therefore, integrating ML approaches with cognitive capabilities can improve the eï¬ectiveness of processing large volumes of information from various distinctive resources.
9) Ambient Backscattering Communication-Enabled CR-IoT System: Ambient backscatter communication (ABC) technology has been re-introduced recently, and is quickly becoming a promising choice for self-sustainable communication systems, as an external power supply or a dedicated carrier emitter is not required. By leveraging existing RF signal resources, ABC technology can support sustainable and independent communications and consequently open up a whole new set of applications that facilitate IoT. Recently, ABC has been introduced in a CR context, in which the secondary transmitter (ST) can communicate with a secondary receiver (SR) by backscattering the primary user (PU) signal, whenever the PU is active. In other words, instead of initiating a CR transmission only when the PU is inactive, the ST can backscatter the PU signal to SR, even when the PU is active. Towards this end, a novel opportunistic ABC framework for RF-powered cognitive radio (CR) networks was recently proposed [91]. The proposed framework considers opportunistic spectrum sensing integrated with ABC and harvest-then-transmit (HTT) operation strategies. It is shown that operating the CR network in a combination of these two modes improves the overall energy eï¬ciency [92]. Thus, ABC can be deployed within either licensed or unlicensed spectrum [93]. A distributed MAC protocol in the ambient backscatter communication system for IoT networks was proposed in [94], which enables each backscatter device (BD) to switch freely among backscatter transmission, receiving and energy harvesting in a distributed way. Thus ambient backscatter communications would be adapted to wearable devices, connected homes, industrial Internet, and miniature embeddable to provide pervasive connectivity [95].
A. Hardware Designs for CR-IoT
The eï¬ective utilization of CRs requires a good hardware design. CR antennas used in one frequency spectrum (cellular) are not the same in size as compared to the ones used in some other spectrum (ISM 2.4 GHz). Furthermore, transmission power levels also vary according to environment. Selection of single-radio or multi-radio is also required [1]. Furthermore, IoT objects are connected to networks through gateways. Thus a gateway design requires ï¬exibility, scalability, security, and energy eï¬ciency. In the case of CR-based IoT objects, additional requirements arise in the form of eï¬cient spectrum resource utilization, particularly in a multi-user scenario [96]. Usually, CR users search for spectrum access individually, but if IoT objects are energy-constrained, gateways may perform spectrum sensing for them. Geo-location-based spectrum searching with history keeping may be a good option. Flexibility and interoperability may be achieved through software deï¬ned radios.
Yet another challenge in CR-based IoT is to manage huge volumes of data. Eï¬ective algorithm design is required to analyze and interpret high-dimensional and nonlinearly separable data which is heterogeneous and diï¬cult to process. Once categorized, decision making is also diï¬cult, keeping the diversiï¬ed nature of applications in mind. In some cases, cognitive applications utilize learning/reasoning algorithms and select processes based on history, which may consume time. Hence, it is necessary to discover advanced knowledge-based algorithms for improved performance.
Spectrum sensing is a preliminary and fundamental step in CRs. IoT objects behaving like CRs have to look for spectrum in a dynamic environment in the presence of a number of PUs, and the problem is boosted when PUs are in the same band. At the same time, diï¬erentiation between licensed and unlicensed signal is also important. Spectrum sensing takes time and consumes energy. Therefore, fast and energy-eï¬cient algorithms should be designed. It is observed that CRs do not perform any task while sensing spectrum. We believe that multiple radios should be employed where one radio performs spectrum sensing while another transfers the data. However, it will be eï¬ective if it is coupled with advanced geo-location-based and history-keeping algorithms. Additionally, we cannot compromise on misdetection probability, but we can compromise on false detection probability. Misdetection relates to a situation where a PU is not detected, and false detection is detecting a PU when there is actually none [97]. If spectrum is sensed ideally, making a decision among searched bands about data transfer is an issue. Of multiple bands, there is a possibility that certain bands do not meet application-speciï¬c QoS requirements. Critical applications need real-time answers, while non-critical applications may compromise on response time. Moreover, assigning spectrum among multiple CRs is also a challenge, and requires resource-shared and application-speciï¬c algorithms.
D. Standardization Activities and Challenges
Standardization eï¬orts in IoT are still in their early stages, and standardization of CR-based IoT is a meager topic to discuss. The ï¬rst and most important problem is related to developing semantic standards as it can accelerate the process in the direction of interoperable solutions. CR-based IoT frameworks may have to support a large number of diversiï¬ed devices for successful semantically operable scenarios. The physical presence of a huge number of devices is connected to a variety of application demands. This requires continuous semantic information sharing. Other key areas of standardization involve communication protocols at each layer, objects selection, and transmission power. The overall beneï¬ts can be achieved if standardization activities are carried out jointly around the globe. Moreover, these eï¬orts have to be streamlined and quick to save cost, which may become another problem in the future.
The existence of several PUs and CRs, and energy levels required for transmission create problems for CRs to sense and decide spectrum eï¬ciently. This creates negative impact on the network. Meanwhile, the multi-user scenario has issues as well. The thing-oriented, semantic-oriented, and internet-oriented nature of IoT already poses problems. When joined with cognitive-capable objects, the problem will be magniï¬ed [98].
The heterogeneity in CR-based IoT frameworks has security problems as we cannot apply the same security levels to all situations. The adaptive capability of CR can become a security problem as an intruder may pretend to be a CR [99]. The security standards have to be applied at all levels, from technology to consumer/business to legal frameworks. Access to information should be easy for validation and monitoring conditions. The introduction of a smart object also introduces privacy issues. A major source of privacy issues is the misuse of application. Privacy is required at the data collection point as CR-based IoT will be a global framework with a variety of technologies and with diverse data. Data is collected using RFID, WSNs, cellular phones, and others, which may lead to severe privacy-related threats. As data is shared along the way, privacy also has to be maintained at data sharing levels. Thus, data anonymization with strict control, management among objects, and identiï¬cation is required [47].
In this article, we have presented the need for cognitive radio networks for IoT. Both technologies are in early stages, but little work has been done in CR-IoT. Consequently, realizing CR-based IoT is still a new paradigm and needs to be studied in detail. It is envisioned that IoT without cognition will just be a burden on existing network infrastructure. However, to support diversity of applications and numerous heterogeneous connected devices, the IoT paradigm poses new challenges to the communication technology. Cognitive radio is considered as a key IoT enabling technology and its integration with future IoT architectures and services will empower the IoT paradigm. We have presented a detailed survey on several interdisciplinary challenges and requirements, such as technical challenges, security, hardware, standard, and business challenges that need to be addressed for the IoT deployment. Integration of emerging techniques such as block chain with CR based IoT were discussed. We have assessed the potential for CR technology in IoT, and we have outlined how CR can empower IoT. Finally we briefed on the research challenges and future research directions in CR-based IoT.
[1] F. A. Awin, Y. M. Alginahi, E. Abdel-Raheem, and K. Tepe, “Technical issues on cognitive radio-based internet of things systems: A survey,” IEEE Access, vol. 7, pp. 97 887–97 908, 2019.
[2] M. S. Mahdavinejad, M. Rezvan, M. Barekatain, P. Adibi, P. Barnaghi, and A. P. Sheth, “Machine learning for internet of things data analysis: a survey,” Digital Communications and Networks, vol. 4, no. 3, pp. 161 – 175, 2018. [Online]. Available: http://www.sciencedirect.com/science/article/pii/S235286481730247X
[3] S. He. (2020, March) Using the internet of things to ï¬ght virus outbreaks. [Online]. Available: https://www.technologynetworks.com/immunology/articles/using-the-internet-of-things-to-ï¬ght-virus-outbreaks-331992
[4] S. S. Mishra and A. Rasool, “Iot health care monitoring and tracking: A survey,” in 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), 2019, pp. 1052–1057.
[5] P. Verma and S. K. Sood, “Fog assisted-iot enabled patient health monitoring in smart homes,” IEEE Internet of Things Journal, vol. 5, no. 3, pp. 1789–1796, 2018.
[6] S. K. Sood and I. Mahajan, “A fog-based healthcare framework for chikungunya,” IEEE Internet of Things Journal, vol. 5, no. 2, pp. 794–801, 2018.
[7] Y. Lin, Y. Lin, and C. Liu, “Aitalk: a tutorial to implement ai as iot devices,” IET Networks, vol. 8, no. 3, pp. 195–202, 2019.
[8] A. Alabdulatif, I. Khalil, A. R. M. Forkan, and M. Atiquzzaman, “Real-time secure health surveillance for smarter health communities,” IEEE Communications Magazine, vol. 57, no. 1, pp. 122–129, 2019.
[9] M. S. Rahman, N. C. Peeri, N. Shrestha, R. Zaki, U. Haque, and S. H. A. Hamid, “Defending against the novel coronavirus (covid-19) outbreak: How can the internet of things (iot) help to save the world?” Health Policy and Technology,Elsevier, 2020.
[10] S. Fahrni, C. Jansen, M. John, T. Kasah, B. Koerber, and N. Mohr. (2020, April) Coronavirus: Industrial iot in challenging times. [Online]. Available: coronavirus-industrial-iot-in-challenging-times
[11] M. Mackenzie. (2020, April) Covid-19: Iot has a limited role in dealing with the current crisis, but could help with future pandemics. [Online]. Available: https://www.sitepoint.com/4-major-technical-challenges-facing-iot-developers
[12] X. Lu, V. Petrov, D. Moltchanov, S. Andreev, T. Mahmoodi, and M. Dohler, “5g-u: Conceptualizing integrated utilization of licensed and unlicensed spectrum for future iot,” IEEE Communications Magazine, vol. 57, no. 7, pp. 92–98, 2019.
[13] F. Li, K. Lam, L. Meng, H. Luo, and L. Wang, “Trading-based dynamic spectrum access and allocation in cognitive internet of things,” IEEE Access, vol. 7, pp. 125 952–125 959, 2019.
[14] Q. Wu, G. Ding, Y. Xu, S. Feng, Z. Du, J. Wang, and K. Long, “Cognitive internet of things: A new paradigm beyond connection,” IEEE Internet of Things Journal, vol. 1, no. 2, pp. 129–143, 2014.
[15] J. Mitola and G. Q. Maguire, “Cognitive radio: making software radios more personal,” IEEE Personal Communications, vol. 6, no. 4, pp. 13–18, 1999.
[16] S. Haykin, “Cognitive radio: brain-empowered wireless communications,” IEEE Journal on Selected Areas in Communications, vol. 23, no. 2, pp. 201–220, 2005.
[17] A. Ahmad, S. Ahmad, M. H. Rehmani, and N. U. Hassan, “A survey on radio resource allocation in cognitive radio sensor networks,” IEEE Communications Surveys Tutorials, vol. 17, no. 2, pp. 888–917, 2015.
[18] H. A. B. Salameh, S. Al-Masri, E. Benkhelifa, and J. Lloret, “Spectrum assignment in hardware-constrained cognitive radio iot networks under varying channel-quality conditions,” IEEE Access, vol. 7, pp. 42 816–42 825, 2019.
[19] A. A. Khan, M. H. Rehmani, and A. Rachedi, “Cognitive-radio-based internet of things: Applications, architectures, spectrum related functionalities, and future research directions,” IEEE Wireless Communications, vol. 24, no. 3, pp. 17–25, 2017.
[20] M. R. Mahmood and M. A. Matin, Towards Cognitive IoT Networks. Springer International Publishing, 2020.
[21] S. K. Sharma, T. E. Bogale, S. Chatzinotas, B. Ottersten, L. B. Le, and X. Wang, “Cognitive radio techniques under practical imperfections: A survey,” IEEE Communications Surveys Tutorials, vol. 17, no. 4, pp. 1858–1884, 2015.
[22] S. Sun, Y. Ju, and Y. Yamao, “Overlay cognitive radio ofdm system for 4g cellular networks,” IEEE Wireless Communications, vol. 20, no. 2, pp. 68–73, 2013.
[23] F. Zeng, J. Xu, Y. Li, K. Li, and L. Jiao, “Performance analysis of underlay two-way relay cooperation in cognitive radio networks with energy harvesting,” Computer Networks, vol. 142, pp. 13 – 23, 2018.
[24] G. Chung, S. Vishwanath, and C. S. Hwang, “On the limits of interweaved cognitive radios,” in 2010 IEEE Radio and Wireless Symposium (RWS), 2010, pp. 492–495.
[25] W. Lee and I. F. Akyildiz, “Spectrum-aware mobility management in cognitive radio cellular networks,” IEEE Transactions on Mobile Computing, vol. 11, no. 4, pp. 529–542, 2012.
[26] S. Gong, P. Wang, and L. Duan, “Distributed power control with robust protection for pus in cognitive radio networks,” IEEE Transactions on Wireless Communications, vol. 14, pp. 1–1, 06 2015.
[27] S. Srikanteswara and D. Choudhury, “A review of tv whitespace portable devices,” in 2010 IEEE Radio and Wireless Symposium (RWS), 2010, pp. 480–483.
[28] M. Nekovee, “A survey of cognitive radio access to TV white spaces,” International Journal of Digital Multimedia Broadcasting, p. 11, 2010.
[29] O. Vermesan, P. Friess, P. Guillemin, S. Gusmeroli, H. Sundmaeker, A. Bassi, I. Jubert, M. Mazura, M. Harrison, M. Eisenhauer, and P. Doody, “Internet of things strategic research roadmap,” Internet of Things – Global Technological and Societal Trends., 01 2009.
[30] RERUM, “Reliable, Resilient and Secure IoT for smart city applications.” [Online]. Available from: https://ict-rerum.eu/., 2015.
[31] Y. Mehta. (2018, August) Addressing the challenges in iot development. [Online]. Available: https://www.iotforall.com/challenges-in-iot-development
[32] R. Mahmoud, T. Yousuf, F. Aloul, and I. Zualkernan, “Internet of things (iot) security: Current status, challenges and prospective measures,” in 2015 10th International Conference for Internet Technology and Secured Transactions (ICITST), 2015, pp. 336–341.
[33] I. Ahmed, A. P. Saleel, B. Beheshti, Z. A. Khan, and I. Ahmad, “Security in the internet of things (iot),” in 2017 Fourth HCT Information Technology Trends (ITT), 2017, pp. 84–90.
[34] K. Balaji, S.and Nathani and R. Santhakumar, “IoT technology, applications and challenges: A contemporary survey,” Wireless Pers Commun, vol. 108, no. 3, pp. 363–388, April. 2019.
[35] S. Xiong, Q. Ni, X. Wang, and Y. Su, “A connectivity enhancement scheme based on link transformation in iot sensing networks,” IEEE Internet of Things Journal, vol. 4, no. 6, pp. 2297–2308, 2017.
[36] L. Tello-Oquendo, I. F. Akyildiz, S. Lin, and V. Pla, “Sdn-based architecture for providing reliable internet of things connectivity in 5g systems,” in 2018 17th Annual Mediterranean Ad Hoc Networking Workshop (Med-Hoc-Net), 2018, pp. 1–8.
[37] G. Zhang, F. Shen, Z. Liu, Y. Yang, K. Wang, and M. Zhou, “Femto: Fair and energy-minimized task oï¬oading for fog-enabled iot networks,” IEEE Internet of Things Journal, vol. 6, no. 3, pp. 4388–4400, 2019.
[38] M. Mangia, A. Marchioni, F. Pareschi, R. Rovatti, and G. Setti, “Chained compressed sensing: A blockchain-inspired approach for low-cost security in iot sensing,” IEEE Internet of Things Journal, vol. 6, no. 4, pp. 6465–6475, 2019.
[39] L. Chettri and R. Bera, “A comprehensive survey on internet of things (iot) toward 5g wireless systems,” IEEE Internet of Things Journal, vol. 7, no. 1, pp. 16–32, 2020.
[40] B. Ray. (2018, August) How to overcome 4 common iot challenges across the board. [Online]. Available: https://www.link-labs.com/blog/iot-challenges
[41] K. L. Lueth. (2019, September) 40+ emerging iot technologies you should have on your radar. [Online]. Available: https://iot-analytics.com/40-emerging-iot-technologies-you-should-have-on-your-radar/
[42] S. Lanzisera, A. R. Weber, A. Liao, D. Pajak, and A. K. Meier, “Communicating power supplies: Bringing the internet to the ubiquitous energy gateways of electronic devices,” IEEE Internet of Things Journal, vol. 1, no. 2, pp. 153–160, 2014.
[43] A. Pal and B. Purushothaman, IoT Technical Challenges and Solutions. Artech House, 01 2017.
[44] A. Banafa. (2017, March) Three major challenges facing iot. [Online]. Available: https://iot.ieee.org/newsletter/march-2017/three-major-challenges-facing-iot.html
[45] B. Dickson. (2017, March) 4 major technical challenges facing iot developers. [Online]. Available: https://www.sitepoint.com/4-major-technical-challenges-facing-iot-developers
[46] F. A. Awin, Y. M. Alginahi, E. Abdel-Raheem, and K. Tepe, “Technical issues on cognitive radio-based internet of things systems: A survey,” IEEE Access, vol. 7, pp. 97 887–97 908, 2019.
[47] S. Yu, G. Wang, X. Liu, and J. Niu, “Security and privacy in the age of the smart internet of things: An overview from a networking perspective,” IEEE Communications Magazine, vol. 56, no. 9, pp. 14–18, 2018.
[48] F. Assaderaghi, G. Chindalore, B. Ibrahim, H. de Jong, M. Joye, S. Nassar, W. Steinbauer, M. Wagner, and T. Wille, “Privacy and security: Key requirements for sustainable iot growth,” in 2017 Symposium on VLSI Technology, 2017, pp. T8–T13.
[49] K. Zhang, X. Liang, R. Lu, and X. Shen, “Sybil attacks and their defenses in the internet of things,” IEEE Internet of Things Journal, vol. 1, no. 5, pp. 372–383, 2014.
[50] D. S. Linthicum, “Connecting fog and cloud computing,” IEEE Cloud Computing, vol. 4, no. 2, pp. 18–20, 2017.
[51] J. J. Kang, K. Fahd, S. Venkatraman, R. Trujillo-Rasua, and P. Haskell-Dowland, “Hybrid routing for man-in-the-middle (mitm) attack detection in iot networks,” in 2019 29th International Telecommunication Networks and Applications Conference (ITNAC), 2019, pp. 1–6.
[52] J. Saleem, M. Hammoudeh, U. Raza, B. Adebisi, and R. Ande, “Iot standardisation: Challenges, perspectives and solution,” in 2018 International Conference on Future Networks and Distributed Systems (ICFNDS), no. 06, 2018, pp. 1–9.
[53] D. M. Milojevic. (2017, April) Digital industrial transformation with the internet of things how can european companies beneï¬t from iot? [Online]. Available: https://www.accenture.com/_acnmedia/PDF-49/Accenture-Digital-Industrial-Transformation-with-the-Internet-of-Things.pdf
[54] M. M. Christine Johansen, Ben Culp. (2017, May) Cisco survey reveals close to three-fourths of iot projects are failing. [Online]. Available: https://www.accenture.com/_acnmedia/PDF-49/Accenture-Digital-Industrial-Transformation-with-the-Internet-of-Things.pdf
[55] R. Sharma. (2017, May) Top 10 challenges enterprises face in iot implementation. [Online]. Available: https://www.ï¬noit.com/blog/enterprise-challenges-in-iot/
[56] M. W. Khan, M. Zeeshan, and K. Shahzad, “On performance analysis of ieee 802.22 phy for cognitive radio based smart grid communications,” in 2018 IEEE International Smart Cities Conference (ISC2), 2018, pp. 1–4.
[57] F. Li, K. Lam, L. Meng, H. Luo, and L. Wang, “Trading-based dynamic spectrum access and allocation in cognitive internet of things,” IEEE Access, vol. 7, pp. 125 952–125 959, 2019.
[58] J. Adu Ansere, G. Han, H. Wang, C. Choi, and C. Wu, “A reliable energy eï¬cient dynamic spectrum sensing for cognitive radio iot networks,” IEEE Internet of Things Journal, vol. 6, no. 4, pp. 6748–6759, 2019.
[59] R. Kishore, S. Gurugopinath, and E. Sangodkar, “Optimal sensor scheduling in energy harvesting-aided cognitive radio networks,” in 2018 IEEE SENSORS, 2018, pp. 1–4.
[60] M. Ozger, O. Cetinkaya, and Ö. B. Akan, “Energy harvesting cognitive radio networking for iot-enabled smart grid,” Mobile Networks and Applications, vol. 23, pp. 956–966, 2018.
[61] Y. Li, X. Cheng, Y. Cao, D. Wang, and L. Yang, “Smart choice for the smart grid: Narrowband internet of things (nb-iot),” IEEE Internet of Things Journal, vol. 5, no. 3, pp. 1505–1515, 2018.
[62] T. Sudha, K. Selvan, V. A. Krishna, Anilkumar, G. Kavya, and P. A. Madhav, “Iot health care monitoring and tracking: A survey,” in Proceedings of the Third International Symposium on Women in Computing and Informatics, August 2015, p. 629–634.
[63] M. A. Hoque and C. Davidson, “Design and implementation of an iot-based smart home security system,” International Journal of Networked and Distributed Computing, vol. 7, pp. 85–92, 2019. [Online]. Available: https://doi.org/10.2991/ijndc.k.190326.004
[64] P. Phunchongharn, E. Hossain, D. Niyato, and S. Camorlinga, “A cognitive radio system for e-health applications in a hospital environment,” IEEE Wireless Communications, vol. 17, no. 1, pp. 20–28, 2010.
[65] M. Chen, W. Li, Y. Hao, Y. Qian, and I. Humar, “Edge cognitive computing based smart healthcare system,” Future Generation Computer Systems, vol. 86, pp. 403 – 411, 2018. [Online]. Available: http://www.sciencedirect.com/science/article/pii/S0167739X17326766
[66] A. Abu Alkheir and H. Mouftah, Cognitive Radio for Public Safety Communications. Wireless Public Safety Networks,Elsevier, 06 2016, pp. 1–22.
[67] S. Ghafoor, P. D. Sutton, C. J. Sreenan, and K. N. Brown, “Cognitive radio for disaster response networks: survey, potential, and challenges,” IEEE Wireless Communications, vol. 21, no. 5, pp. 70–80, 2014.
[68] W. Yao, A. Yahya, F. Khan, Z. Tan, A. U. Rehman, J. M. Chuma, M. A. Jan, and M. Babar, “A secured and eï¬cient communication scheme for decentralized cognitive radio-based internet of vehicles,” IEEE Access, vol. 7, pp. 160 889–160 900, 2019.
[69] J. Eze, S. Zhang, E. Liu, and E. Eze, “Cognitive radio-enabled internet of vehicles: a cooperative spectrum sensing and allocation for vehicular communication,” IET Networks, vol. 7, no. 4, pp. 190–199, 2018.
[70] V. Gotarane and S. Raskar, “Iot practices in military applications,” in 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), 2019, pp. 891–894.
[71] F. T. Johnsen, Z. ZieliÅski, K. Wrona, N. Suri, C. Fuchs, M. Pradhan, J. Furtak, B. Vasilache, V. Pellegrini, M. Dyk, M. Marks, and M. KrzysztoÅ, “Application of iot in military operations in a smart city,” in 2018 International Conference on Military Communications and Information Systems (ICMCIS), 2018, pp. 1–8.
[72] N. Komninos, E. Philippou, and A. Pitsillides, “Survey in smart grid and smart home security: Issues, challenges and countermeasures,” IEEE Communications Surveys Tutorials, vol. 16, no. 4, pp. 1933–1954, 2014.
[73] N. Ul Hassan, C. Yuen, and M. Bershgal Atique, “Exploiting qos ï¬exibility for smart grid and iot applications using tv white spaces,” in 2017 IEEE International Conference on Communications (ICC), 2017, pp. 1–6.
[74] I. Parvez, N. Islam, N. Rupasinghe, A. I. Sarwat, and . Güvenç, “Laa-based lte and zigbee coexistence for unlicensed-band smart grid communications,” in SoutheastCon 2016, 2016, pp. 1–6.
[75] K. Katzis, R. Jones, and G. Despotou, “Totally connected healthcare with tv white spaces,” Studies in health technology and informatics, vol. 238, pp. 68–71, 07 2017.
[76] V. Chamola, V. Hassija, V. Gupta, and M. Guizani, “A comprehensive review of the covid-19 pandemic and the role of iot, drones, ai, blockchain, and 5g in managing its impact,” IEEE Access, vol. 8, pp. 90 225–90 265, 2020.
[77] S. Gurugopinath, R. Muralishankar, and H. N. Shankar, “Diï¬erential entropy-driven spectrum sensing under generalized gaussian noise,” IEEE Communications Letters, vol. 20, no. 7, pp. 1321–1324, 2016.
[78] S. Hartinah, H. Prakoso, and K. Anwar, “Routing of mobile cognitive radio base station for disaster recovery networks,” in 2018 International Conference on Electrical Engineering and Informatics (ICELTICs), 2018, pp. 1–6.
[79] C. Wang, L. Zhang, Z. Li, and C. Jiang, “Sdcor: Software deï¬ned cognitive routing for internet of vehicles,” IEEE Internet of Things Journal, vol. 5, no. 5, pp. 3513–3520, 2018.
[80] P. Wassell, “3 military applications of the internet of things,” https://www.augmate.io/3-military-applications-of-the-internet-of-things/, April 2018.
[81] J. Donaldson, “Rï¬d and iot technology: Improving military and defense applications from end to end,” https://mojix.com/rï¬d-iot-technology-military-defense/, October 2019.
[82] M. Anwer, A. saad, and A. Ashfaque, “Security of iot using block chain: A review,” in 2020 International Conference on Information Science and Communication Technology (ICISCT), 2020, pp. 1–5.
[83] A. Panarello, N. Tapas, G. Merlino, F. Longo, and A. Puliaï¬to, “Blockchain and iot integration: A systematic survey,” Sensors, vol. 18, p. 2575, 08 2018.
[84] D. He, K. R. Choo, N. Kumar, and A. Castiglione, “Ieee access special section editorial: Research challenges and opportunities in security and privacy of blockchain technologies,” IEEE Access, vol. 6, pp. 72 033–72 036, 2018.
[85] J. H. Jeon, K. Kim, and J. Kim, “Block chain based data security enhanced iot server platform,” in 2018 International Conference on Information Networking (ICOIN), 2018, pp. 941–944.
[86] C. H. Lee and K. Kim, “Implementation of iot system using block chain with authentication and data protection,” in 2018 International Conference on Information Networking (ICOIN), 2018, pp. 936–940.
[87] M. Mahdavinejad, M. Rezvan, M. Barekatain, P. Adibi, P. Barnaghi, and A. Sheth, “Machine learning for internet of things data analysis: A survey,” Digital Communications and Networks, 10 2017.
[88] T. Clancy, J. Hecker, E. Stuntebeck, and T. O’Shea, “Applications of machine learning to cognitive radio networks,” Wireless Communications, IEEE, vol. 14, pp. 47 – 52, 09 2007.
[89] M. S. Mahdavinejad, M. Rezvan, M. Barekatain, P. Adibi, P. Barnaghi, and A. P. Sheth, “Machine learning for internet of things data analysis: a survey,” Digital Communications and Networks, vol. 4, no. 3, pp. 161 – 175, 2018. [Online]. Available: http://www.sciencedirect.com/science/article/pii/S235286481730247X
[90] R. G. Babu, A. Nedumaran, and A. Sisay, “Machine learning in iot security performance analysis of outage probability of link selection for cognitive networks,” in 2019 Third International conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), 2019, pp. 15–19.
[91] R. Kishore, S. Gurugopinath, P. C. Sofotasios, S. Muhaidat, and N. Al-Dhahir, “Opportunistic ambient backscatter communication in rf-powered cognitive radio networks,” IEEE Transactions on Cognitive Communications and Networking, vol. 5, no. 2, pp. 413–426, 2019.
[92] ——, “Opportunistic ambient backscatter communication in rf-powered cognitive radio networks,” in 2019 IEEE Wireless Communications and Networking Conference (WCNC), 2019, pp. 1–6.
[93] L. Zhang, Y. Liang, and M. Xiao, “Spectrum sharing for internet of things: A survey,” IEEE Wireless Communications, vol. 26, no. 3, pp. 132–139, 2019.
[94] X. Cao, Z. Song, B. Yang, M. A. Elmossallamy, L. Qian, and Z. Han, “A distributed ambient backscatter mac protocol for internet-of-things networks,” IEEE Internet of Things Journal, vol. 7, no. 2, pp. 1488–1501, 2020.
[95] F. Jameel, T. Ristaniemi, I. Khan, and B. M. Lee, “Simultaneous harvest-and-transmit ambient backscatter communications under rayleigh fading,” J Wireless Com Network 2019,Springer, vol. 166, no. 2019, 2019.
[96] R. Kishore, S. Gurugopinath, S. Muhaidat, P. C. Sofotasios, O. A. Dobre, and N. Al-Dhahir, “Sensing-throughput tradeoï¬ for superior selective reporting-based spectrum sensing in energy harvesting hcrns,” IEEE Transactions on Cognitive Communications and Networking, vol. 5, no. 2, pp. 330–341, 2019.
[97] J. Adu Ansere, G. Han, H. Wang, C. Choi, and C. Wu, “A reliable energy eï¬cient dynamic spectrum sensing for cognitive radio iot networks,” IEEE Internet of Things Journal, vol. 6, no. 4, pp. 6748–6759, 2019.
[98] M. A. Shah, S. Zhang, and C. Maple, “Cognitive radio networks for internet of things: Applications, challenges and future,” in 2013 19th International Conference on Automation and Computing, 2013, pp. 1–6.
[99] M. H. Khadr, H. B. Salameh, M. Ayyash, S. Almajali, and H. Elgala, “Securing iot delay-sensitive communications with opportunistic parallel transmission capability,” in 2019 IEEE Global Communications Conference (GLOBECOM), 2019, pp. 1–6.